
Mobile devices, especially smartphones, are something more private than computers that we often share with the family. Privacy is important and there is always the possibility that we want to save something that we do not want anyone else to see. There are many options to achieve this, such as creating a compressed file with a password, but in this way we are implying that we have something to hide, which is true. If we want to hide something and no one knows that we are hiding it, we can always hide files within an image.
This is possible thanks to a simple terminal command. That and taking the correct steps in the correct order. What we will do is basically create a compressed file whose thumbnail in the file manager is an image, one that we can even open like any other. The only thing that can make the "intruders" suspicious is that we put many gigabytes into an image, but that is now up to each one of us. Here we are going to explain the process.
Hide files in a fully functional image
Before detailing the steps to follow, we are going to say what we are going to do: we are going to take a folder, in my case Secret Folder, which will be the one that will have all the files, we are going to compress said folder and create the file FolderSecreta.zip, join it to an image call Image.png which will be "the disguise" or "cover" and create a file that will only show one image but will have all the files inside, which in my case will be Capture.png. The steps to follow would be the following:
- We put the image and the folder that we want to hide (FolderSecreta) within the same folder, whatever it is. For example, in Documents.
- If we have not done it already, we put all the files that we want to hide in FolderSecreta. I have removed the space in the folder name to make things easier in the terminal.
- We compress the folder. We can do this by right clicking and using our default compressor.
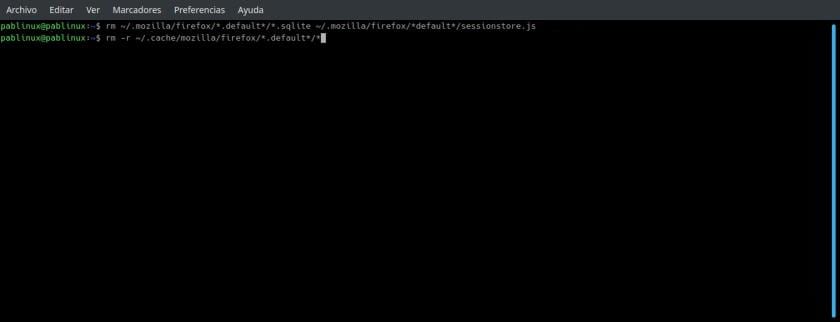
- We open the terminal.
- We go to the folder where FolderSecreta.zip and Imagen.png are together, in my case the command would be cd / home / pablinux / Desktop.
- The next step is to "concatenate" the SecretFolder.zip and Image.png files into the Capture.png output file. The command for my example would be the following:
cat Imagen.png CarpetaSecreta.zip > Captura.png
- Finally, we can delete all the files, except "Capture.png" which is where all the hidden data is, but not before checking that we can unzip it as we will explain later.
Esteganography, hide a file within others
Now you can do the test: if we open the image, the program that opens it will tell us that it has a normal weight, such as a 2mb capture like the one I have used, but by right clicking on the image and entering its properties, we will see that the size is somewhat larger. TO This process, hide files within others, it is called Steganography, What is it "the study and application of techniques that allow to hide messages or objects, within others, called carriers, to be sent and so that the fact is not perceived. That is, it tries to hide messages within other objects and in this way establish a covert channel of communication, so that the act of communication itself goes unnoticed by observers who have access to that channel.«.
For unzip the file newly created, it is not enough to open it with an application to unzip, it is not even worth changing the extension to .zip and trying to unzip it. We will have to use another command, this one easier to remember. In the case of my example, the command would be:
unzip Captura.png
The only thing we will see after pressing Enter is that the folder that we had compressed in step 3 appears. Where we will see something else will be in the terminal, which in my case shows something like the following:
pablinux @ k1904: ~ / Desktop $ unzip Capture.png
Archive: Capture.png
warning [Capture.png]: 703579 extra bytes at beginning or within zipfile
(attempting to process anyway)
creating: SecretFolder /
inflating: FolderSecreta / Magnifier.png
inflating: FolderSecreta / Pablinux.jpg
creating: FolderSecreta / Disco-Dingo_WP_4096x2304 /
inflating: FolderSecreta / Disco-Dingo_WP_4096x2304 / Disco-Dingo_WP_4096x2304.png
Has the explanation in this article helped you? And now, tell me: what will you hide on your PC? Or better not tell me ...
Crypto is overvalued, apparently ...
https://lunaticgeek.com/esteganografia/
Apart from the trouble that these computer enthusiasts can get you into, when they discover something new they even think it is new and start writing about it without even proving what they are saying.
«We compressed the folder. We can do this by right clicking and using our default compressor. If we want, we can give it a password. »
So if we want we can put a password, it will be if we want to lose our precious data if we put a password, because in his article he does not explain how to deal with this situation.
I find it horrible that people who do not know about computers can lose information they want to hide by following in the footsteps of another computer enthusiast who does not even test what he writes.
Pablinux reads a little more about the cat command in case some user decides to set a password to his zip and then he gets a nasty surprise when he unzips and sees that all the folders are empty, if any. And just get an exit skipping.
What if you try unzip -P?
You get the same "skipping" result, so if you have used this method with a password and deleted the original files, you are going to be in for an unpleasant surprise, because it indicates that you can set a password but not how to deal with this situation.
That well, I knew it in Windows with binary copy. I like the syntax better on Linux.
I've been doing that for years in Windows, because of the fact that the work email blocks emails with Zip attachments but does not say anything about PNGs.
Compress the Zip, from DOS / CMD copy / b image.png + thing.zip
Then rename the PNG to Zip and extract with anything serious (7zip, bandizip, WinRAR, WinZip ...)
And passwords can be used if cal.
PS: this is not steganography. Enter the info 3n the pixels it is (for example, the last bit of each pixel or so)