
Meltdown and Specter They are the trends of recent days, practically nothing else is talked about and it is no wonder, since they are probably the most important vulnerabilities in history. They seriously affect the security of our systems and if the system belongs to a company or you have relevant data, the problem is much more serious. However, it is always thought that only desktop computers, laptops, servers and supercomputers are affected, but the damage goes further and affects many more devices, such as those based on ARM cores and includes tablets, smartphones, and some devices. IoT, industrial, home automation, even connected cars.
As you well know, it is not something unique to Linux by any means, but rather affects various operating systems, also Microsoft Windows and macOS are affected by it, without forgetting iOS and Android. Therefore few escape these threats, although it is true that certain CPU architectures are spared and that if we have an AMD chip, the chances of exploiting these vulnerabilities are probably less, but that does not mean that there is no risk.
What is the current situation for Linux?

Linux basically moves the worldAlthough many believe that it is a system that is rarely used, it is the opposite. Possibly it has failed in the aspect that it was created for the desktop and that is precisely the only sector where it is a minority compared to the almighty Windows and compared to a good portion that Mac has. If we go to embedded or embedded devices, servers, supercomputers, etc., Linux is dominant and it is precisely the Internet servers in which it becomes vital and without it it can practically be said that the Internet would fall ...
That is why in Linux reacted before than in any other system to solve the problems that Meltdown and Specter could leave behind. Already Linus Torvalds He spoke on the matter with a few harsh words to Intel and if you take a look at the LKML you will see that it is a matter of concern and is the order of the day. And his right-hand man and number two in Linux kernel development, Greg Kroah-Hartman has done it too. For more information you can consult your personal blog where you will find enough information.
- Meltdown: Basically Greg has commented that regarding Meltdown it can be ended on x86 by choosing to include CONFIG_PAGE_TABLE_ISOLATION, a page table isolation (PTI) that computers with AMD processors, not affected by it, should avoid to avoid problems with performance. You may even have known that some computers with an AMD chip have stopped booting because the Windows patch has generated serious problems. PTI will be included in Linux 4.15 by default, but due to its importance in terms of security it will be included in previous versions such as LTS 4.14, 4.9 and 4.4 ... and probably over time the patch will be incorporated into many other versions, but patience because it implies an overload of work for developers. And they are also running into patch issues like vDSO in some virtual machine setups. Regarding ARM64, slightly affected by Meltdown which is a major problem for Intel, the chips of many mobile devices and other devices also need a patch, although it seems that it will not merge with the main kernel tree in the short term ( maybe on Linux 4.16, although Greg has commented that they may never arrive due to the amount of prerequisites that patches need to be approved) and therefore it is advised to make use of specific kernels, that is, Android Common Kernel in its branches 3.18, 4.4 and 4.9.
- Spectre: the other problem affects more architectures, and is more complicated to deal with. It seems that we will not have a good solution in the short term and we will have to coexist with this problem for a while. In its two variants, it needs the system to be patched and some development communities of certain distros have already begun to release patches to mitigate it, but the solutions provided are diverse and for the moment they will not be integrated as part of the main branch of the kernel until The best solution is seen before CPU designers come up with the best solution (redesign their chips). The solutions have been studied and they are finding some problems along the way, such as the greater ignorance about Specter. Developers need time to figure out how to deal with the problem, and Greg himself has commented that “This is going to be an area of research in the coming years to find ways to mitigate possible problems involving hardware, which will also try to predict them in the future before they happen.«.
- Chromebooks- If you have a Google laptop you will be glad to know that you can see the status of the work they are doing to solve Meltdown on this list.
How can I easily check if I am affected?

In order not to go around consulting tables or lists of microprocessors, here we propose a script that they have created to be able to easily check if we are affected or not, we simply have to download and run it and it will tell us whether or not we are in danger from Specter and Meltdown. The instructions or steps to follow are simple:
git clone https://github.com/speed47/spectre-meltdown-checker.git cd spectre-meltdown-checker/ sudo sh spectre-meltdown-checker.sh
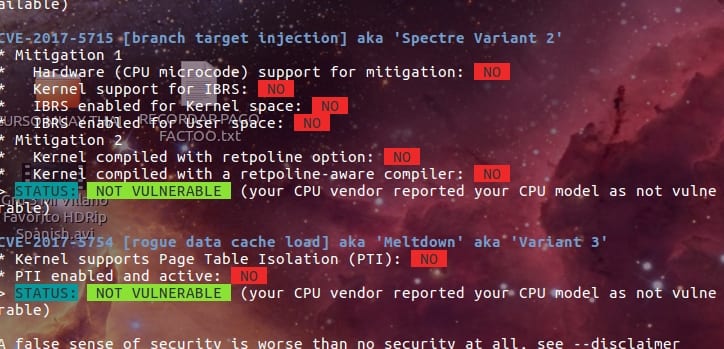
After executing this, a red box will appear to indicate if we are vulnerable to Meltdown or Specter or a green indicator in case we are safe from the variants of these vulnerabilities. In my case, for example, having an AMD APU (without even having updated the system), the result has been:
In case the result has been in red VULNERABLE, read the following section ...
What to do if I am affected?
The best solution, as some say, is to switch to a CPU or microprocessor that is not affected by the problem. But this is not feasible for many of the users due to lack of budget or other reasons. Also, manufacturers like Intel they continue to sell affected microprocessors and that have been launched recently, such as Coffee Lake, since microarchitectures usually have long development times and now they are working on the design of future microarchitectures that will appear on the market in coming years, but all the chips that are being commercialized now and that will probably be commercialized in the coming months will continue to be affected at the hardware level.
Therefore, in the case of suffering from this disease and needing to "fix" it, we have no choice but to patch our operating system (don't forget the browsers, etc.), whatever it may be, and also update all the software that we have. If have well configured the update system It was already very important, now more than ever you must keep up to date with the updates, since with them will come the patches that solve the Meltdown and Specter problem from the software side, not without a loss of performance as we already said ...
The solution is not complicated for the user, we don't have to do anything "special", just make sure our distro's developer has released the update for Meltdown and Specter and that we have it installed. More information about it.
If you want, you can check if the patch was installed (if needed) for Meltdown on your distro with this command:
dmesg | grep "Kernel/User page tables isolation: enabled" && echo "Tienes el parche! :)" || echo "Ooops...no tienes la actualización instalada en tu kernel! :("
*Beware of Ubuntu kernel 4.4.0-108-genericSome users have reported problems on their computers when booting after the update and have had to revert to a previous version. Canonical seems to have solved it in 4.4.0-109-generic ...
Loss of performance: there was talk of 30% in some cases, but it will depend on the microarchitecture. In older architectures, the performance loss can be very severe because the performance gains that these architectures have are mainly based on the improvements provided by the OoOE execution and the TLB ... In more modern architectures, it is spoken of between 2% and 6% depending on the type of software running for home users, possibly in data centers the losses are much higher (over 20%). As recognized by Intel itself, after downplaying what was coming to them, the performance in processors prior to Haswell (2015) the performance drop will be much worse than that 6% even for normal users ...
Do not forget to leave your comments with your doubts or suggestions ...
Very good post, thank you very much and congratulations. Also with an AMD APU, I ran the script and everything was fine. Some of lime, others sand: and to think that when I joined this team it was because of an excellent promotion that appeared years ago in a chain store and as time passed I cursed my destiny given the hell experienced by proprietary AMD drivers for GNU / Linux (After expiration, I opted to give myself to the free Drivers and I'm happy, it works better than Windows 10). I have friends seriously affected by the problem and their devices really did go back to the days of Pentium 4, having i3 and i5 processors.
Specter and Meltdown mitigation detection tool v0.28
Checking for vulnerabilities against running kernel Linux 4.14.12-1-MANJARO # 1 SMP PREEMPT Sat Jan 6 21:03:39 UTC 2018 x86_64
CPU is Intel (R) Core (TM) i5-2435M CPU @ 2.40GHz
CVE-2017-5753 [bounds check bypass] aka 'Specter Variant 1'
* Checking count of LFENCE opcodes in kernel: NO
> STATUS: VULNERABLE (only 21 opcodes found, should be> = 70, heuristic to be improved when official patches become available)
CVE-2017-5715 [branch target injection] aka 'Specter Variant 2'
* Mitigation 1
* Hardware (CPU microcode) support for mitigation: NO
* Kernel support for IBRS: NO
* IBRS enabled for Kernel space: NO
* IBRS enabled for User space: NO
* Mitigation 2
* Kernel compiled with retpoline option: NO
* Kernel compiled with a retpoline-aware compiler: NO
> STATUS: VULNERABLE (IBRS hardware + kernel support OR kernel with retpoline are needed to mitigate the vulnerability)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Kernel supports Page Table Isolation (PTI): YES
* PTI enabled and active: YES
> STATUS: NOT VULNERABLE (PTI mitigates the vulnerability)
A false sense of security is worse than no security at all, see –disclaimer
In this part I say yes, and in the image you say no.
* PTI enabled and active: YES
what should I do
Hello,
I don't use Manjaro, but I assume they will be working on an update. So keep your system as up to date as possible. The latest versions of the kernel also implement solutions if you want to install them ...
A greeting and thanks for reading!
In Ubuntu they solved the Meltdown problem with the kernel update, 4.13.0.
I use Peppermint 8 and doing the Meltdown vulnerability test no longer throws me vulnerable.
Greetings.
Specter and Meltdown mitigation detection tool v0.28
Checking for vulnerabilities against running kernel Linux 4.14.13-041413-generic # 201801101001 SMP Wed Jan 10 10:02:53 UTC 2018 x86_64
CPU is AMD A6-7400K Radeon R5, 6 Compute Cores 2C + 4G
CVE-2017-5753 [bounds check bypass] aka 'Specter Variant 1'
* Checking count of LFENCE opcodes in kernel: NO
> STATUS: VULNERABLE (only 29 opcodes found, should be> = 70, heuristic to be improved when official patches become available)
CVE-2017-5715 [branch target injection] aka 'Specter Variant 2'
* Mitigation 1
* Hardware (CPU microcode) support for mitigation: NO
* Kernel support for IBRS: NO
* IBRS enabled for Kernel space: NO
* IBRS enabled for User space: NO
* Mitigation 2
* Kernel compiled with retpoline option: NO
* Kernel compiled with a retpoline-aware compiler: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
CVE-2017-5754 [rogue data cache load] aka 'Meltdown' aka 'Variant 3'
* Kernel supports Page Table Isolation (PTI): YES
* PTI enabled and active: NO
> STATUS: NOT VULNERABLE (your CPU vendor reported your CPU model as not vulnerable)
A false sense of security is worse than no security at all, see –disclaimer
Wasn't it solved by having the latest kernel?
regards
Is there a way to measure how performance affects us before and after applying the patch ???