
da An saki masu binciken tsaro na IBM kwanakin baya sun gano wani sabon gidan malware da ake kira "ZeroCleare", wanda aka kirkira ta kungiyar masu fashin kwamfuta ta kasar Iran APT34 tare da xHunt, wannan malware an tsara shi ne kan masana'antun masana'antu da makamashi a Gabas ta Tsakiya. Masu binciken ba su bayyana sunayen kamfanonin da abin ya shafa ba, amma sun gudanar da bincike kan cutar cikakken bayani mai shafi 28.
ZeroCleare yana shafar Windows kawai tunda kamar yadda sunan ta ya bayyana ta hanyar hanyar bayanan shirin (PDB) na Ana amfani da fayil din ta na binary don aiwatar da wani mummunan hari wanda ya sake yin rikodin babban rikodin boot boot (MBR) da bangare kan injunan Windows masu rauni.
ZeroCleare an ƙididdige shi azaman malware tare da ɗabi'a da ke kama da ta "Shamoon" (wata cuta ce da aka yi magana akai saboda an yi amfani da ita don kai hare-hare kan kamfanonin mai tun a shekarar 2012) Kodayake Shamoon da ZeroCleare suna da halaye da halaye iri ɗaya, masu bincike sun ce biyun ɓarna ce ta daban.
Kamar Shamoon malware, ZeroCleare yana amfani da halastaccen mai sarrafa faifai mai suna "RawDisk by ElDos", don sake rubuta babban rikodin boot boot (MBR) da kuma ɓangarorin diski na takamaiman kwamfutocin da ke aiki da Windows.
Kodayake mai sarrafawa Su biyun ba a sanya hannu ba, malware tana sarrafawa don aiwatar da shi ta loda maɓallin VirtualBox m amma ba a sa hannu ba, amfani da shi don ƙetare hanyar tabbatar da sa hannu kuma shigar da direban ElDos wanda ba a sa hannu ba.
An ƙaddamar da wannan ɓarnar ta hanyar kai hare-hare na zalunci don samun damar isa ga tsarin tsaro mara ƙarfi. Da zarar maharan sun harba na'urar da ke niyya, sai su yada malware ta hanyar sadarwar kamfanin a matsayin matakin karshe na kamuwa da cutar.
“Mai tsabtace ZeroCleare wani bangare ne na matakin karshe na harin baki daya. An tsara shi don tura nau'i biyu daban-daban, wanda ya dace da tsarin 32-bit da 64-bit.
Babban jigilar abubuwan da ke faruwa a kan na'urori 64-bit sun haɗa da amfani da direba mai sa hannu mara ƙarfi sannan kuma amfani da shi a kan na'urar da aka kera don ba ZeroCleare damar tsallake layin ɓoye kayan aikin Windows da kuma ƙetare wasu tsare-tsaren tsarin aiki waɗanda ke hana direbobin Mara izini suna gudana akan 64-bit inji ', karanta rahoton IBM.
Ana kiran mai sarrafawa na farko a cikin wannan sarkar soy.exe kuma sigar da aka gyara ce ta mai kwatancen direban Turla.
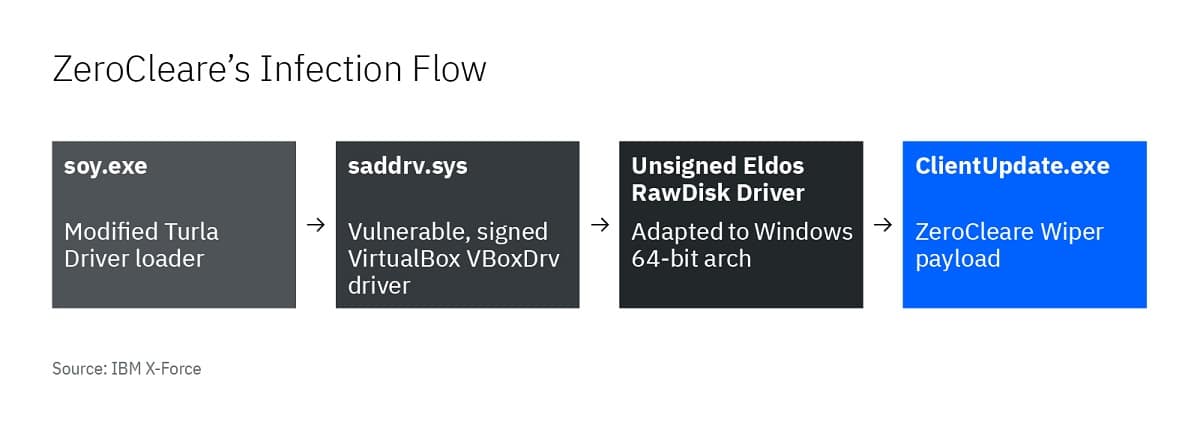
Ana amfani da wannan mai kula don ɗora sigar mai rauni ta mai kula da VirtualBox, wanda maharan ke amfani dashi don lodawa direban EldoS RawDisk. RawDisk shine ingantaccen mai amfani da aka yi amfani dashi don ma'amala da fayiloli da ɓangarori, kuma maharan Shamoon suma sunyi amfani dashi don samun damar MBR.
Don samun dama ga ainihin na'urar, ZeroCleare yana amfani da direba mai rauni da gangan da kuma rubutun PowerShell / Batch mai ƙeta don kewaya sarrafa Windows. Ta hanyar ƙara waɗannan dabaru, ZeroCleare ya bazu zuwa na'urori da yawa akan cibiyar sadarwar da abin ya shafa, yana shuka iri na harin ɓarna wanda zai iya shafar dubban na'urori da haifar da lamuran da zasu iya ɗaukar watanni kafin su warke sarai.
Ko da yake da yawa daga cikin kamfen din APT masu binciken sun nuna mayar da hankali kan leken asiri ta hanyar yanar gizo, wasu daga cikin rukuni guda kuma suna aiwatar da ayyukan barna. A tarihi, yawancin waɗannan ayyukan an yi su ne a Gabas ta Tsakiya kuma sun mai da hankali kan kamfanonin makamashi da wuraren samarwa, waɗanda ke da mahimmancin ƙasa.
Kodayake masu binciken ba su daga sunayen kowace kungiya 100% wanda aka danganta wannan malware, a matakin farko sun yi sharhi cewa APT33 ya halarci ƙirƙirar ZeroCleare.
Sannan daga baya IBM yayi da'awar cewa APT33 da APT34 sun kirkiri ZeroCleare, amma jim kadan bayan fitar da takaddar, sai yanayin ya canza zuwa xHunt da APT34, kuma masu binciken sun yarda da cewa basu da tabbaci dari bisa dari.
A cewar masu binciken, Hare-haren ZeroCleare ba na cin zarafi bane kuma suna bayyana kamar ayyukan da aka shirya akan takamaiman sassa da ƙungiyoyi.