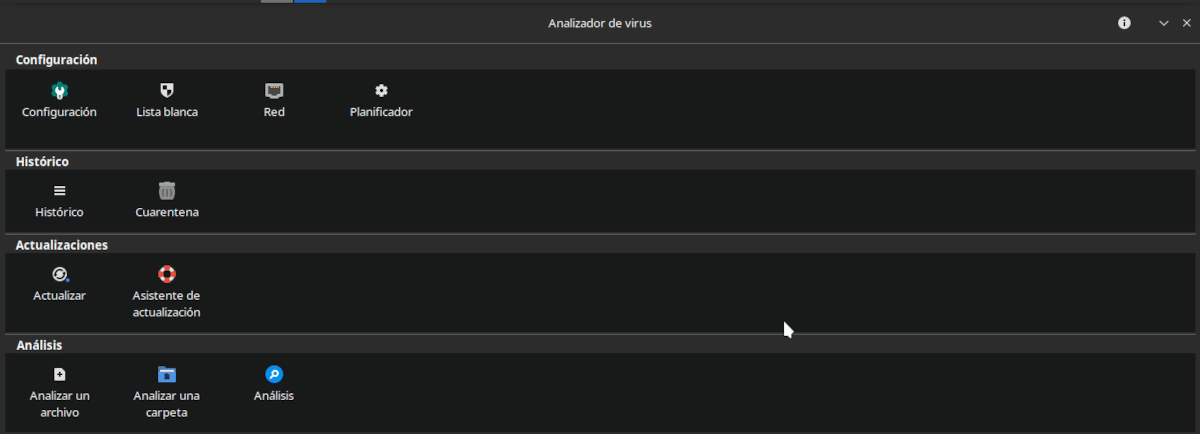
ClamTK is the graphical interface to control the open source antivirus ClamAV
Do the products respond to a need or create it? Although the consensus within the community is that Linux doesn't need an antivirus, someone went to the trouble of developing them. In fact, there are quite a few free and open source and commercial alternatives.
In this article we are going to see what is ClamTK, the graphical interface for ClamAV, an open source antivirus solution and when you should install it.
Do we need an antivirus on Linux?
For a long time, Linux users convinced ourselves that we were immune to malicious code. However, in recent years We should have changed our minds. Attacks against Linux have been increasing since 2016 and nearly a third of malware targets this operating system.
Partly, This increase in attacks is because large organizations turned to Linux as a reliable system capable of performing critical tasks for corporate servers more efficiently and at a lower cost. than their proprietary counterparts. Hence, it became a legitimate target for attackers since the data they store and the networks they support are enormously valuable.
Some vulnerabilities exploited by attackers are:
Use of cross-platform languages
The use of cross-platform applications such as those programmed in Java (which runs under a virtual machine) it is a source of entry for malicious software. YES these applications work with sensitive data, it does not matter what operating system you are using.
Use of content managers
Linux is the majority operating system in servers. And many servers use content managers like Drupal and WordPress. These tools are usually installed with a high degree of permissions including FTP write access. PTo expand functions, these content managers usually use third-party add-ons that tend to have a high cost, which is why many irresponsible people tend to download them from alternative sources. And, even if they are downloaded from official sites, programming errors that cause vulnerabilities cannot be ruled out.
asymptomatic carrier
There is nothing to prevent a Linux computer from spreading malware to vulnerable systems. Linux computers receive and send emails with attachments that may be infected.
Not keeping up with updates
In the case of common services such as Apache and FTP, maintaining a regular update is as vital as breathing for living beings.. Regular updates reduce risks, but many people often view these critical tasks as a waste of time and ignore notifications asking them to do so. Other times it is because the updates would force you to stop using programs that would no longer be compatible.
Use of Samba
Samba is a suite of programs that allow Windows and Linux to be integrated into the same network. When using Samba, Linux shares look and behave like any other Windows share. That is to say that Linux permissions no longer work. Windows security tools are not prepared to detect malware for other platforms.
Using Windows tools to scan the contents of Linux shares over a network runs the risk of leaving traffic exposed. In the case of equipment used in businesses, some of the most damaging attacks were carried out by disgruntled employees seeking harm or financial gain.
Increased system complexity
With the use of technology such as containers and virtualization, it is possible to have multiple versions of an operating system or multiple operating systems installed at the same time. That is why Unless you have an automated tool installed to manage them, updates are impossible to track. Hence, the security risks increase.

As companies have relied more on Linux for their infrastructure, attackers have made it a target.
Poor definition of roles and privileges
Linux has a clear system of roles and privileges that must be carefully respected. The root user is the one who has the power to access anywhere and make any changes within the system. There are some users who, without being Root, have the same privileges.
Normal users are denied access to certain sensitive parts of the system, but with respect to the parts they have access to, there are also various restrictions on what they can do.
The rule is to assign each user only the privileges they need, but because it's time-consuming, complex, or lacking in knowledge, those rules are often not followed.
Lack of training for system administrators
Trained sysadmins are rare and expensive. Many times people are hired without sufficient knowledge and who are overloaded with work. Even in the cases of professionals, they tend to be tied to certain technologies without verifying that they are the right ones in each case.
What is ClamTk
ClamTK can be installed from the Software Center of the main Linux distributions
It is true that almost everything I mention above refers to servers and large corporate networks. Also that Most of the information about the need to install antivirus on Linux comes precisely from Linux antivirus developers. Let me quote a paragraph from a website whose name we will avoid.
Not all antivirus solutions are the same. As mentioned above, native Linux antiviruses are superior to a Windows-based solution. But there are big differences between native antivirus tools that you should take the time to research to make the right choice for your organization. For example, open source solutions may attract users at first glance because they are advertised as free. However, the maintenance and configuration requirements are more complex and cost security teams more time and effort. Other critical factors like ease of use, performance, detection rates, support, scalability, and centralized management should also be carefully considered before making a decision.
I return to the question at the beginning of the article. Do the products respond to a need or do they create it? The increase in vulnerabilities is true. It is also that on single-user computers where installations are applied frequently and programs are installed from the official repositories, there should be no problem. Much less if you don't open attachments.
In any case, it is worth taking precautions and ClamTK comes in here
ClamTK is the graphical interface of the open source antivirus ClamAV. This is an open source technology for detection of Trojans, viruses, malware, and other malicious threats.
ClamAV Features
- Scanning using the command line or with graphical interface (Installing ClamTK)
- Email filtering.
- Threat Database Updater and digital signatures with the possibility of doing it through scripts.
- Update several times a day of the threat database.
- Support for all formats of e-mail.
- Built-in support for various archive formats, including ZIP, RAR, Dmg, Tar, GZIP, BZIP2, OLE2, Cabinet, CHM, BinHex, SIS, and others.
- Integrated support for ELF executables and portable executable files packed with UPX, FSG, Petite, NsPack, wwpack32, MEW, Upack and obfuscated with SUE, Y0da Cryptor and others.
- Built-in support for popular document formats, including MS Office and MacOffice files, HTML, Flash, RTF, and PDF.
If anything can be said about ClamTK it is that its interface is more utilitarian than pretty. Just the functions ordered by category and represented with an icon. When we place the pointer on each icon, it shows us a brief explanation of the characteristics of each function. However, it is not very intuitive and requires a bit of research or familiarity with using antivirus.
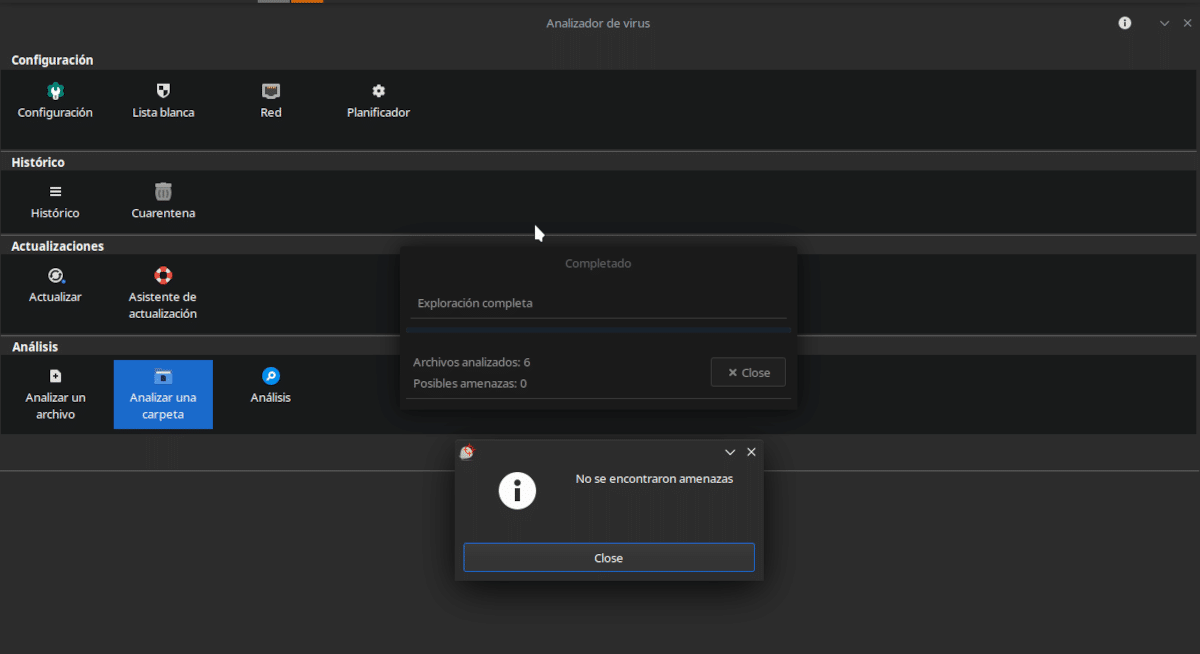
ClamTK allows us to analyze files and folders, both manually and automatically.
The different ClamTK options are:
- Configuration: Determine what and how is scanned.
- White list: He determines that he is not considered a threat.
- Net: Gives ClamAV the privileges to access the Internet.
- Analysis: Determines the time when the analysis is done or the database is updated.
- Historic: Shows previous scans.
- Quarantine: Allows you to restore or delete isolated files.
- Updates: Lets you review installed updates and update mode.
- Update Wizard: Allows you to determine how updates are received.
- Parse a file: Do I really have to explain it? A file is selected within the explorer and OK is pressed.
- Scan a folder: The same, but with folders.
- Analysis: Shows the results of the analysis of a file.
In my opinion, ClamTK (available in the repositories of all Linux distributions) does not take advantage of all the capabilities of ClamAV, but, for its use in home equipment is flexible enough. Remember that any of us interact with multimedia content and open attachments that we receive in emails or messaging services. Even if they don't infect our computer, we can always prevent them from infecting someone else's.
I always make the comparison with the story of the 3 little pigs. The wolf managed to get into the first two houses. And, if he had taken his time, he would have made it with the third.
I would like an article with alternatives to ClamAV in linux, I don't know if it is because of the use of ClamTk but, at least on my machine (which is very old and modest in resources), it consumes a gross amount both in execution (processor) and in memory (ram) while doing a scan.