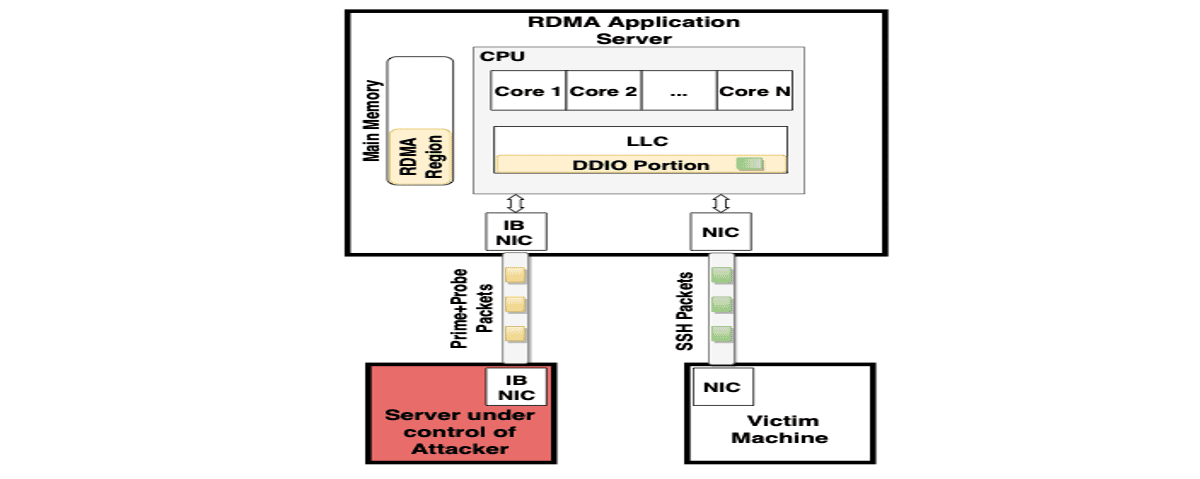
A group of researchers from the University of Amsterdam and the Swiss Higher Technical School in Zurich developed the "NetCAT" network attack technique (Network Cache ATtack) that allows to use data analysis methods from third-party channels to remotely determine the keys a user presses while working in an SSH session. The problem only manifests itself on servers that use RDMA (Remote Direct Memory Access) and DDIO (Direct I / O to Data) technologies.
Intel believes the attack is difficult to implement in practice.a, as it requires the attacker's access to the local network, in addition to the conditions and organization host communications using RDMA and DDIO technologies, which are generally used in isolated networks, for example, where clusters operate.
The method used for the attack resembles Throwhammer vulnerability, which allows the content of individual bits in RAM to be changed through network packet manipulation on RDMA systems.
The researchers comment that:
The new problem is the result of minimizing delays by using the DDIO mechanism, which provides direct interaction between the network card and other peripheral devices with the processor cache (during processing of network card packets, data is cached and retrieved from the cache, without accessing memory).
Thanks to DDIO, the processor cache also includes data generated during malicious network activity.
The NetCAT attack relies on the fact that network cards cache data actively, and the speed of packet processing in modern local networks is sufficient to influence cache filling and determine the presence or absence of data in the cache through analysis of data transmission delays.
When using interactive sessions, for example via SSH, a network packet is sent immediately after pressing a key, that is, delays between packets are correlated with delays between keystrokes.
Using statistical analysis methods and taking into account that the delays between keystrokes generally depend on the position of a key on the keyboard, it is possible with some probability to recreate the input information. For example, most people tend to type "s" after "a" much faster than "g" after "s."
The information cached by the processor also allows you to judge the exact time of packets sent by the network card when processing connections such as SSH.
By generating a certain flow of traffic, an attacker can determine when new data appears in the cache associated with a certain activity in the system.
To analyze the contents of the cache, the Prime + Probe method is used, which consists of filling the cache with a set of reference values and measuring the access time to them when filling to determine the changes.
It is possible that the technique proposal can be used to determine not only keystrokes, but also other types of sensitive data cached by the CPU.
In our attack, we take advantage of the fact that the DDIO-enabled application server has a shared resource (the last-level cache) between the CPU cores and the network card. We reverse engineer the important properties of DDIO to understand how the cache is shared with DDIO.
An attack can potentially be carried out when RDMA is disabled, but without RDMA its effectiveness is reduced and execution is significantly complicated.
It is also possible to use DDIO to organize a covert communication channel used to transfer data after a server has been compromised, bypassing security systems.
Source: https://www.vusec.net