It is not the only service for it, but Mozilla has also made Firefox Monitor available to you. Some of the existing services are a bit dubious, perhaps it transmits more confidence that Mozilla is behind this. The reason is that some of the dubious services could use the data they enter to know that you are vulnerable and to be able to carry out some type of attack with it. Well, having said that, let's see what it is about ...
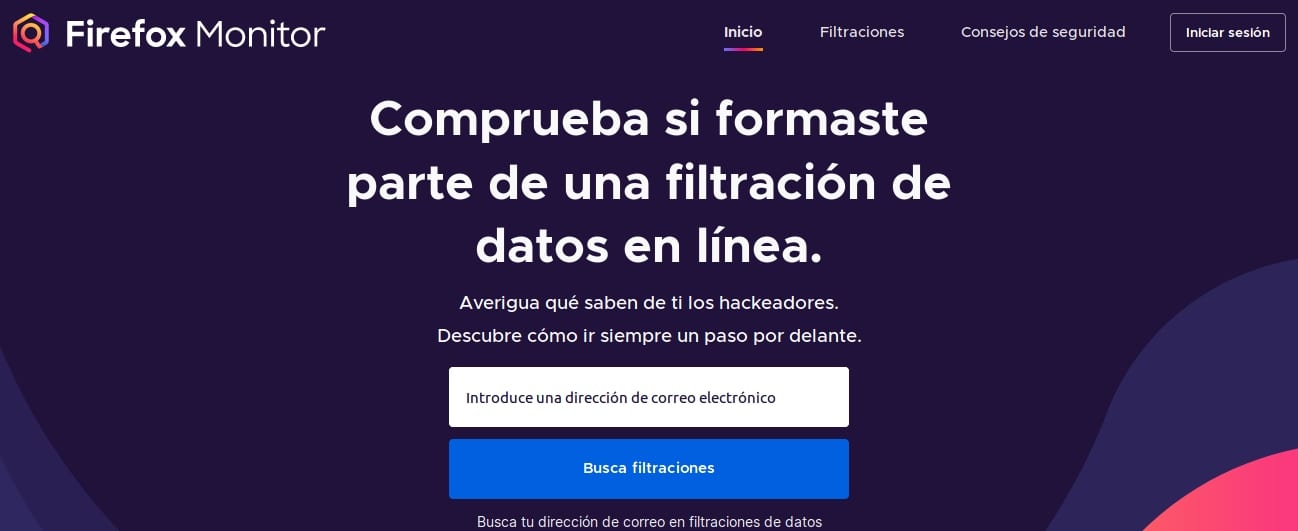
Mozilla Firefox Monitor allows you to enter your email addresses to contrast with the database they have if have been victims of some type of cyber attack. With this, you will be able to know if your accounts have been compromised and the credentials, such as your password, are available to cybercriminals. So you can act and change your credentials to protect your services.
The steps you must follow are:
- Log in in the official website.
- Put it email you want to check in the box.
- Push the button Look for Leaks.
- Then will search in the database if there are matches and it will show you the results. If it has not been compromised or if your address has been compromised. Unfortunately, the service only reaches compromised accounts until 2017 ... So if it has been attacked in 2018 or 2019, no coincidence will appear ...
What to do after checking it?
- Whether your address has not been compromised or it has been, it is recommended to change your password and put a robust. That is, one of more than 8 characters and that is a combination of uppercase, lowercase, numbers and symbols. Never words found in the dictionary.
- In addition to changing the password, it would be interesting if you add Two-Step Verification in your mail service (if possible). That way, even though they may compromise your password, it won't be so easy to access.