Tor is a project whose main objective is the development of a distributed communications network with low latency and superimposed on the internet, en does not reveal the identity of its users, that is, their IP address remains anonymous. Under this concept, the browser has gained much popularity and has become widely used in all parts of the world, generally its use is attributed to illegal activities given its characteristics of allowing anonymity.
Although the browser is offered to users in order to offer safer browsing and above all to offer its anonymity. ESET researchers released recently they have discovered the spread of a fake version of the Tor browser by strangers. Since a compilation of the browser was made that was positioned as the official Russian version of the Tor browser, while its creators had nothing to do with this compilation.
ESET's Principal Malware Researcher Anton Cherepanov said that the investigation had identified three bitcoin wallets used by hackers since 2017.
'Each wallet contains a relatively large number of small transactions; we consider this to be a confirmation that these wallets were used by the trojanized Tor browser "
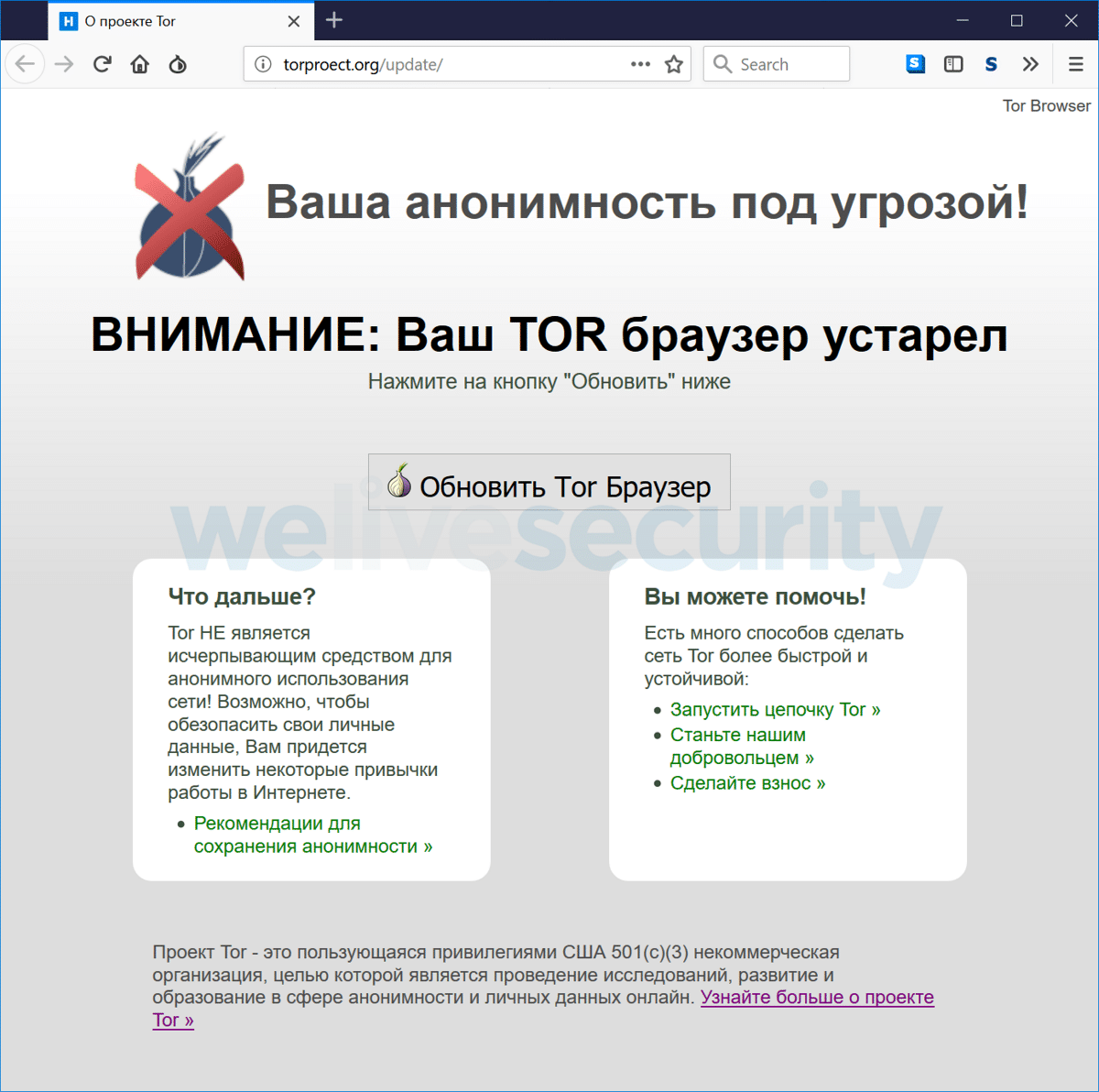
The goal of this modified version of Tor was to replace Bitcoin and QIWI wallets. To mislead users, the creators of the compilation registered the domains tor-browser.org and torproect.org (differs from the official site torproJect.org in the absence of the letter "J", which many Russian-speaking users go unnoticed).
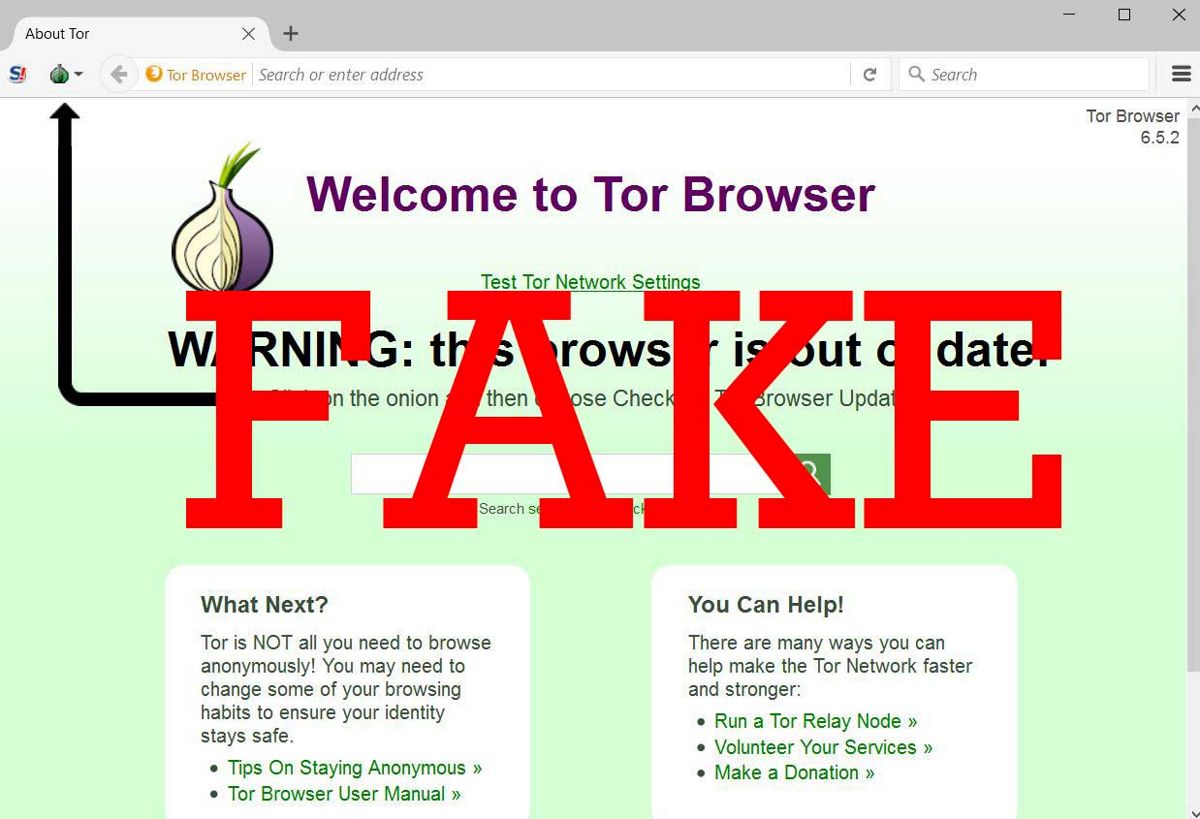
The design of the sites was styled like the official Tor site. The first site showed a warning page about using an outdated version of the Tor browser and a proposal to install an update (where the provided link offers compilation with the Trojan software) and in the second the content repeated the page to download the Tor browser.
It is important to mention that the malicious version of Tor was configured for Windows only.
Since 2017, the malicious Tor browser has been promoted in various forums in Russian, in discussions related to darknet, cryptocurrencies, avoiding Roskomnadzor locks and privacy issues.
To distribute the browser on pastebin.com, many pages have also been created that are optimized to be displayed at the top of search engines on topics related to various illegal operations, censorship, names of famous politicians, etc.
Pages advertising a fake version of the browser on pastebin.com have been viewed more than 500 times.
The fictitious set was based on the Tor Browser 7.5 code base And in addition to the built-in malicious features, minor user agent tweaks, disabling digital signature verification for plugins, and locking the update installation system, it was identical to the official Tor browser.
The malicious insert consisted of attaching a content controller to the HTTPS plugin Everywhere regular (added additional script.js script to manifest.json). The remaining changes were made at the configuration settings level and all binary parts were kept in the official Tor browser.
The script built into HTTPS Everywhere, when each page was opened, went to the admin server, which returned the JavaScript code that should be executed in the context of the current page.
The management server worked as a hidden Tor service. Through the execution of JavaScript code, attackers can organize the interception of the contents of web forms, the substitution or hiding of arbitrary elements on the pages, the display of fictitious messages, etc.
However, when analyzing the malicious code, only the code to replace the details of QIWI and Bitcoin wallets on the darknet payment acceptance pages was recorded. In the course of the malicious activity, 4.8 Bitcoins were accumulated in the wallets to replace them, which corresponds to approximately 40 thousand dollars.