
The guys from the development team Offensive Security are pleased to announce a new version of their Kali Linux computer security system. This would be the second so far this year, with which in this new version improvements and changes are added to the distro focused on Pentesting.
If you don't know the distro yet let me tell you a little about it. Kali Linux founded and maintained by Offensive Security Ltd, is a distribution derived from Debian Testing, formerly known under the name of BackTrack which was based on Ubuntu and known today as Kali Linux, this being a Rolling Release distribution, Kali Linux features the GNOME Shell desktop and several some modifications, andIt is adapted with applications for auditing and IT security in general.
What's new in Kali Linux 2018.2
Among the changes and corrections that we find in this new version of Kali Linux we can state that the kernel of the system has been updated with what is already by default within the system images the Linux Kernel 4.15 with which it includes x86 corrections and x64 for Specter and Meltdown vulnerabilities, which caused too much trouble in the last few months of last year.
Bug fixes in Kali Linux 2018.2
As well a bug affecting Gnome NetworkManager has been resolved, as a connection could not be established through OpenVPN since it was disconnected immediately.
Has also added better support for AMD GPUs and support for AMD Secure Encrypted Virtualization, as this can encrypt the virtual machine memory so that even the hypervisor cannot access it.
Also the tool jsql injection received support because in the previous version of Kali Linux this tool stopped working when it was updated by the user.
Of the others bugs fixed we found that btscanner fixed a bug that caused this to crash when used and also a minimal fix to the background of the Kali desktop theme not working for 2560x1600 resolutions
Improvements in Kali Linux 2018.2
In the improvements that Kali Linux 2018.2 has received Metasploit stands out mainly which the developers realized that during the use of this a great amount of time is spent unnecessarily writing exploits.
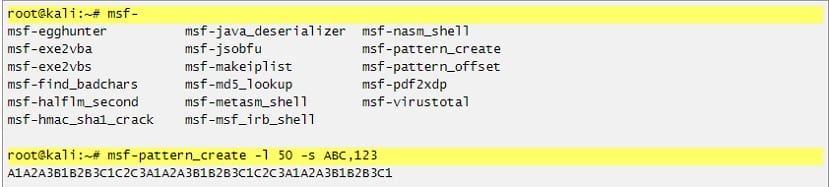
Like for example pattern_create, pattern_offset, nasm_shell which all these useful scripts are hidden in / usr / share / metasploit-framework / tools / exploit, that is why from metasploit-framework_4.16.34-0kali2 , now you can make use of all these scripts directly, since Links to all of them in the PATH, each one of them.
Updated packages in Kali Linux 2018.2
In this version of Kali Linux several tools have been updated among which we can dstake Reaver v1.6.4, PixieWps v1.4.2, burpsuite 1.7.32, Burp Suite, Hashcat v4.0.0 and more.
Finally, in this new version of Kali Linux we found the new Ropper tool that was added to the system, with it you can get the information about files in different file formats such as binaries, deb packages, rpm, slices, sections, etc. In addition, it is possible to edit the binaries and edit the header fields.
How to get Kali Linux 2018.2?
If you are already a Kali Linux user, you just have to go to your terminal and execute the following command that will be in charge of updating your system, so it is necessary to be connected to the network to be able to carry out this process.
apt update && apt full-upgrade
Now if you don't have the system and you want to have the system image, you can download it from its official website.
How to download Kali Linux 2018.2?
We just have to head to the following link and in the download section we must download the appropriate system image for our equipment, this depends on what type of processor the computer has where you will install it.
You will only have to burn the ISO of the system on a DVD or a USB to be able to install it on your computer.
I have already installed it several times but none of them recognizes the network card integrated in my laptop and it does not recognize UTP either (try live mode but still), and with respect to the desktop the same thing happens to me :(