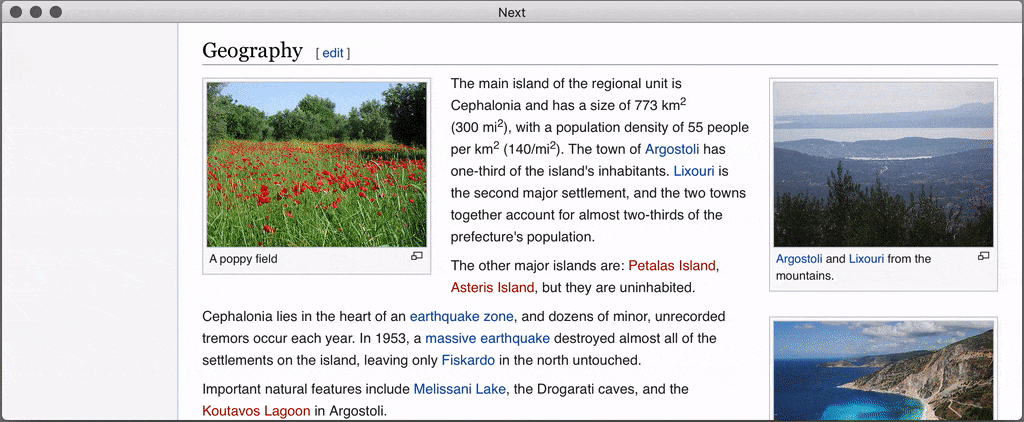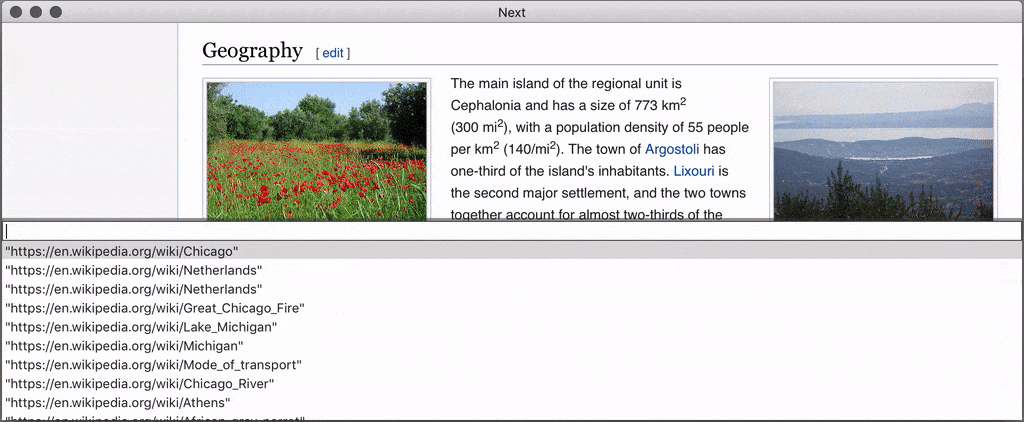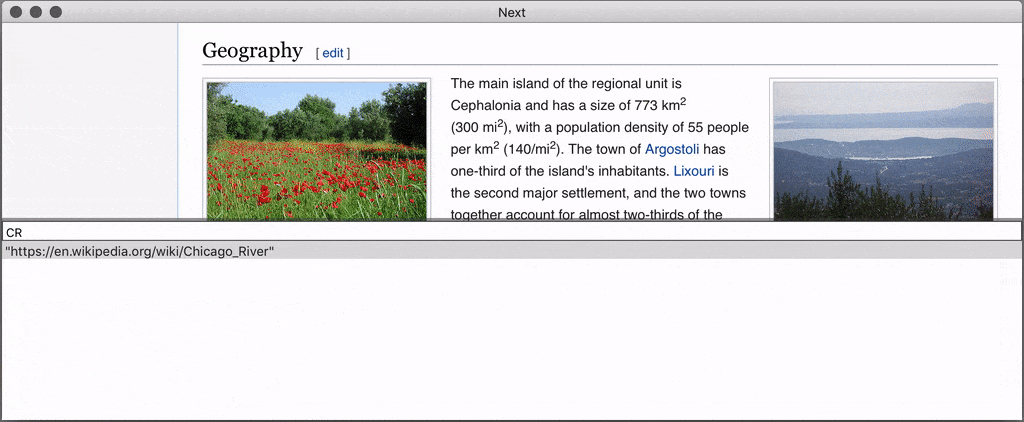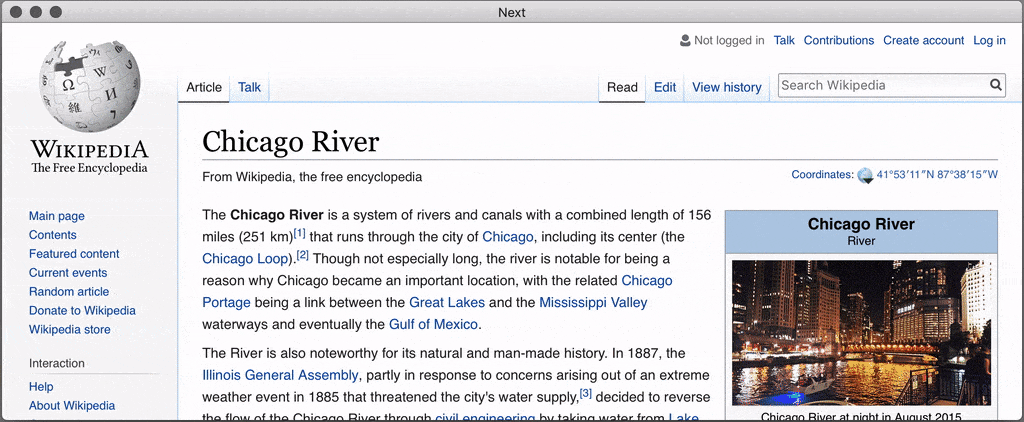
Next is an extensible, keyboard-oriented web browser fully designed for advanced users, this web browser is unique because it does not expose an API, it is completely open and programmable so there is no need to restart it to test your changes. And unlike similar projects (Konqueror or Vimperator that died, Qutebrowser…), it is not tied to a particular rendering engine.
Next is built around two components: the core and one port per platform. It currently has two platforms: GTK / WebKit and Qt / Blink. The core is in Common Lisp, the port in GTK in C and Qt in Python (PyQt, Webengine).
Both components communicate via D-Bus. It also makes use of XML-RPC before D-Bus and the change greatly benefits the browser.
Besides the mentioned features of this web browser (fuzzy browsing is really cool), Other practical features can be highlighted, such as:
- navigation by title
- ad blocking (per domain)
- improved coarse / fuzzy selection
- Keyboard shortcuts in Vim
- a download manager
- a NoScript mode
- a »back-end» based on Blink, the Chrome rendering engine (added to the WebKit back-end)
- support for proxy servers, hence Tor
How to use
As mentioned, this web browser is geared for use with the keyboard, so has a series of keyboard shortcuts that define the different functions that can be performed with this browser.
The quick launch keys are as follows:
- Cl: Load URL in tab
- ML: Load URL in a new tab
- Cx b: Change tab
- Cb: History backwards
- Cf: Forwarding history
- Cx Cc: Leave
- TAB: Full Candidate (in minibuffer)
- Symbols represent modifiers:
- C: Control key
- S: Super (Windows key, command key)
- M: Meta (Alt key, Option key)
- s: Shift key
The following keys exist as special keys:
BACKSPACE, DELETE, ESCAPE, HYPHEN, RETURN, SPACE, TAB, Left, Right, Up, Down
How to install Next Browser on Linux?
For those who are interested in being able to install this web browser, they should know that its method is easy for GNU / Linux and macOS, since the developers offer an all-in-one Guix file and it is in MacPorts.
In the case of Guix, it is enough to implement it in the system, we do this by following the instructions that I share below.
First we download:
wget https://ftp.gnu.org/gnu/guix/guix-binary-1.0.1.system.tar.xz.sig gpg --keyserver pool.sks-keyservers.net \ --recv-keys 3CE464558A84FDC69DB40CFB090B11993D9AEBB5 gpg --verify guix-binary-1.0.1.system.tar.xz.sig
Then we access as root and we must type the following:
cd /tmp tar --warning=no-timestamp -xf \ guix-binary-1.0.1.system.tar.xz mv var/guix /var/ && mv gnu / mkdir -p ~root/.config/guix ln -sf /var/guix/profiles/per-user/root/current-guix \
~root/.config/guix/current GUIX_PROFILE="`echo ~root`/.config/guix/current" ; \ source $GUIX_PROFILE/etc/profile cp ~root/.config/guix/current/lib/systemd/system/guix-daemon.service \ /etc/systemd/system/ systemctl start guix-daemon && systemctl enable guix-daemon mkdir -p /usr/local/bin cd /usr/local/bin ln -s /var/guix/profiles/per-user/root/current-guix/bin/guix mkdir -p /usr/local/share/info cd /usr/local/share/info
for i in /var/guix/profiles/per-user/root/current-guix/share/info/* ; do ln -s $i ; done guix archive --authorize < \
~root/.config/guix/current/share/guix/ci.guix.gnu.org.pub
We exit the root session and we can install the browser by typing:
guix pull guix install next
Although they also offer the source code of the browser to make the compilation for those who prefer this method. The code can be downloaded from the link below.
Finally for those who are Arch Linux users, Manjaro, Arco Linux or any other distribution based on Arch Linux, they can install the browser from AUR.
They just have to type the following command in a terminal:
yay -S next-browser-git
Its developer recommends that to improve security while browsing the Internet, you can run Next with Firejail on Linux.
Firejail is a SUID program that reduces the risk of security breaches by restricting the execution environment of untrusted applications that use Linux namespaces and seccomp-bpf. Allows a process and all its descendants to have their own private view of globally shared kernel resources, such as the network stack, process table, and mount table.
To do this, just open a terminal and execute the following command in it:
firejail --ignore = nodbus next-gtk-webkit
