Shadowsocks Outline only supports AEAD cipher suites
Recently the launch of the new version of the proxy server outline-ss-server 1.4, which uses the Shadowsocks protocol to hide the nature of the traffic, bypass firewalls, and fool packet inspection systems.
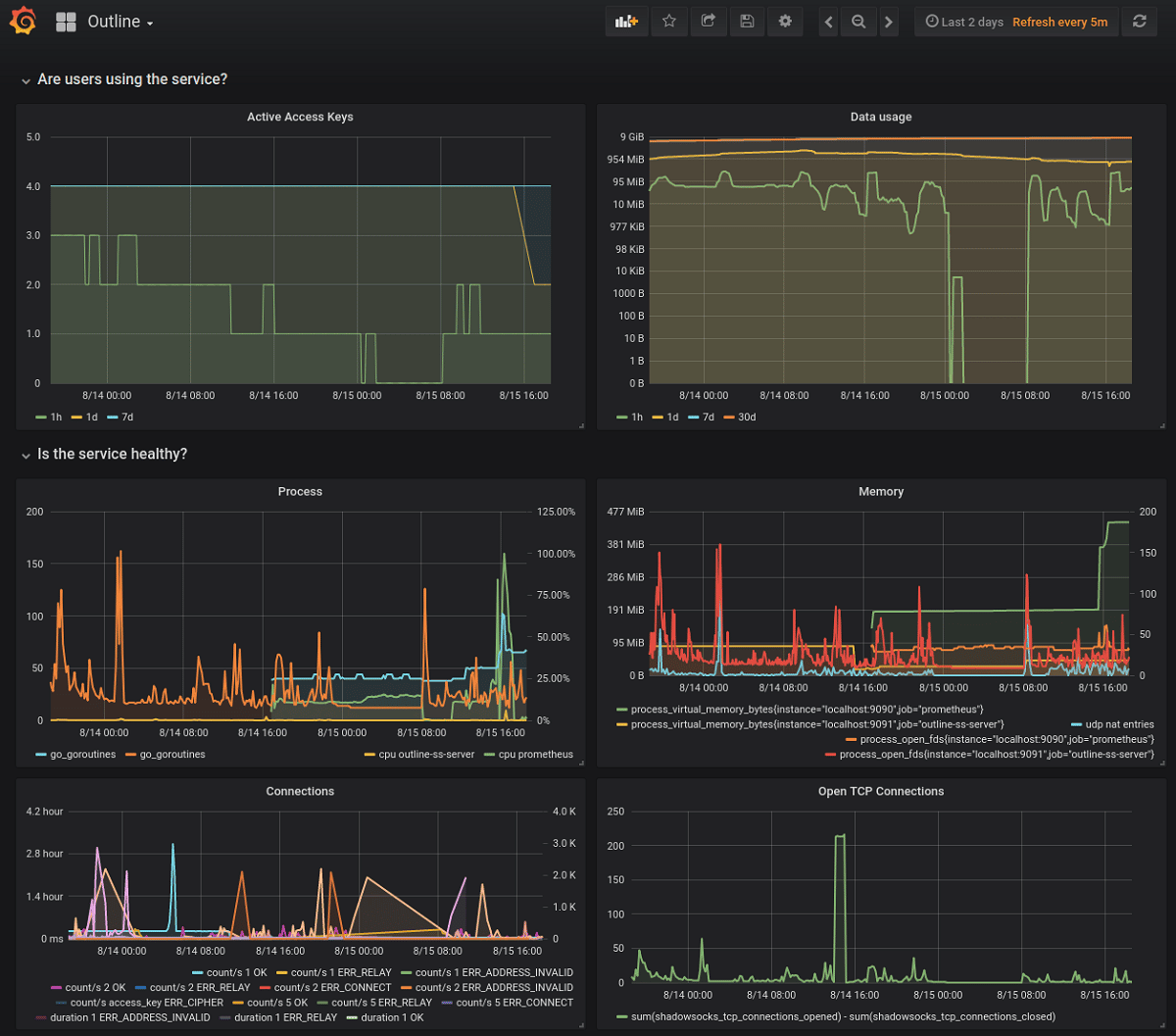
The server is being developed by the Outline project, which also provides a client application binding and control interface that allows the user to quickly deploy multi-tenant Shadowsocks servers based on ss-schema server in public cloud environments or on your own computer.
In addition to this, it is possible to manage them through a web interface and organize user access by password. Jigsaw is responsible for code development and maintenance, a division within Google created to develop tools to circumvent censorship and enable the free exchange of information.
About Outline-ss-server
The differences between outline-ss-server and go-shadowsocks2 come down to support for connecting multiple users. through a single network port, the ability to open multiple network ports to receive connections, support for hot restarts and configuration updates without interrupting connections, built-in monitoring and traffic measurement tools based on the prometheus .io platform .
It is worth mentioning that recently, the main activity of the Shadowsocks project has been focused on the development of a new server in the Rust language, and the Go implementation has not been updated for more than a year and is noticeably behind in functionality.
The ss-schema server also adds protection against polling requests and replay attacks of traffic. An attack via verification requests aims to determine the presence of a proxy, for example an attacker can send data sets of different sizes to the target Shadowsocks server and analyze how much data the server will read before determining an error and closing the connection. . A replay attack is based on hijacking a session between a client and a server and then attempting to resend the hijacked data to determine the presence of a proxy.
To protect against attacks via verification requests, the outline-ss-server server, when bad data arrives, it does not terminate the connection and does not show an error, instead, it continues to receive information, acting as a kind of black hole. To protect against replay, the data received from the client are also checked for repetitions using checksums stored for the last thousand handshake sequences (max 40 thousand, size is set at server startup and consumes 20 bytes of memory per sequence). To block repeated responses from the server, all server handshake sequences use HMAC authentication codes with 32-bit labels.
In terms of the level of traffic hiding, the Shadowsocks protocol in the ss-scheme server implementation is close to the Obfs4 pluggable transport in the anonymous Tor network. The protocol was created to bypass China's traffic censorship system (the "Great Firewall of China") and allows you to hide traffic forwarded through another server quite effectively (traffic is problematic to identify due to connection of a random seed and the simulation of a continuous flow).
SOCKS5 is used as the protocol for proxy requests: A SOCKS5-compliant proxy is started on the local system, which funnels traffic to a remote server from which requests are executed. The traffic between the client and the server is placed in an encrypted tunnel, hiding the fact that the creation is the main task of Shadowsocks. TCP and UDP tunneling is supported, as is the creation of arbitrary tunnels, not limited to SOCKS5, by using plugins that resemble pluggable transports in Tor.
For those interested in the project, you should know that Outline-ss-server is written in Go and released under the Apache 2.0 license. The go-shadowsocks2 proxy server code, created by the Shadowsocks developer community, is used as the basis.