Every time there rarer and more sophisticated malware, as well as new types of cyber attacks. But the techniques to stop this type of malicious code are also having some changes and revolutions, from the use of AI technology to make detection systems more intelligent, to many other innovative methods to protect themselves.
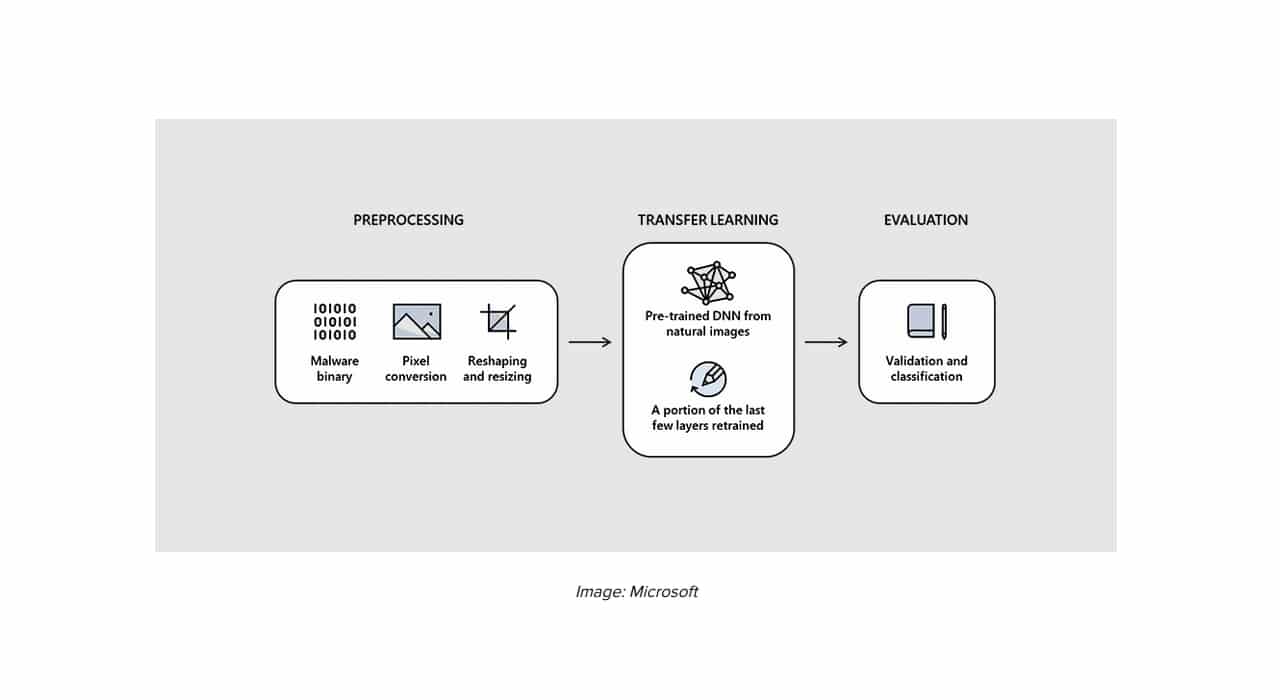
Intel and Microsoft have collaborated to bring a new and original way to detect malware by analyzing the code of suspicious programs in a very particular way. It consists of generating an image from the code that you want to analyze and searching it for threats thanks to the use of an AI.
Although it seems strange, the name of this project is called STAMINA (STAtic Malware-as-Image Network Analysis). It is basically an implementation of a technique that transforms suspicious code into a grayscale image so that an AI will then analyze it for similar patterns to detect malicious code by comparing patterns.
The image is also reduced so that the AI does not have to analyze millions of pixels and can do lighter scan without affecting the final result. This AI has already been trained, since it has been feeding its algorithm through malware samples with more than 2.2 million hashes of infected executable files so that it learns from them the common pattern they have and thus can detect them.
Un weird method that goes from binary code to pixels for an AI to analyze this data. Certainly something that had not been seen so far. And according to the researchers involved, it appears that it can identify and classify malware with 99,07% accuracy. With a false positive rate of 2,58% (which is still relatively high). So it is promising, but it needs to be refined, in addition to improving your work with large files, where it becomes even less efficient ...
For more information - Project whitepaper