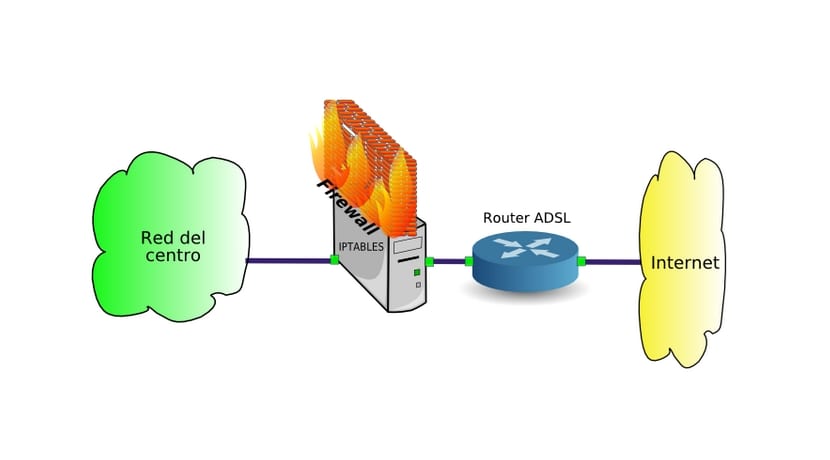
For configure a firewall or firewall in Linux, we can make use of iptables, a powerful tool that seems forgotten by many users. Although there are other methods, such as ebtables and arptables to filter traffic at the link level, or Squid at the application level, iptables can be very useful in most cases, implementing good security in our system at the traffic and transport level of net.
The Linux kernel implements iptables, a part that takes care of filtering packets and that in this article we teach you to configure in a simple way. Simply put, iptables identifies what information can and cannot enter, isolating your team from potential threats. And although there are other projects like Firehol, Firestarter, etc., many of these firewall programs use iptables ...
Well, Let's get down to work, with examples you will understand everything better (for these cases it is necessary to have privileges, so use sudo in front of the command or become root):
The general way to use iptables to create a filter policy is:
IPTABLES -ARGUMENTS I / O ACTION
Where -ARGUMENT is the argument we will use, normally -P to establish the default policy, although there are others such as -L to see the policies that we have configured, -F to delete a created policy, -Z to reset the byte and packet counters, etc. Another option is -A to add a policy (not the default), -I to insert a rule at a specific position, and -D to delete a given rule. There will also be other arguments to point to -p protocols, –sport source port, –dport for destination port, -i incoming interface, -o outgoing interface, -s source IP address and -d destination IP address.
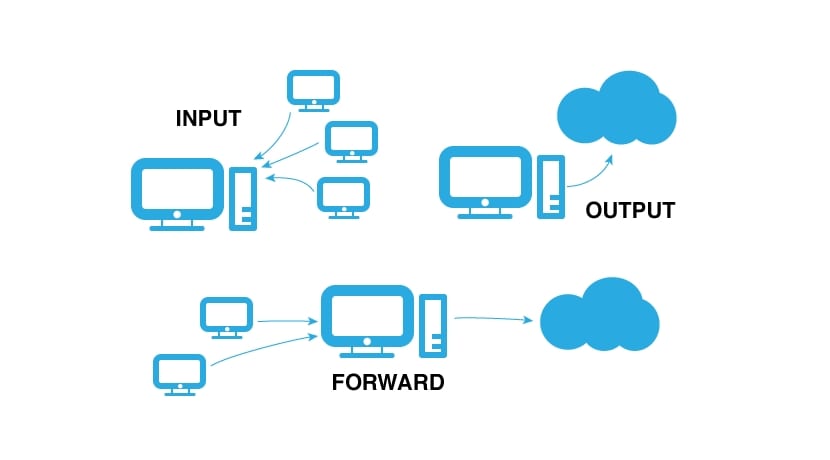
Furthermore I / O would represent if politics It is applied to the INPUT input, to the OUTPUT output or it is a FORWARD traffic redirection (there are others such as PREROUTING, POSTROUTING, but we will not use them). Finally, what I have called ACTION can take the value ACCEPT if we accept, REJECT if we reject or DROP if we eliminate. The difference between DROP and REJECT is that when a packet is rejected with REJECT, the machine that originated it will know that it has been rejected, but with DROP it acts silently and the attacker or origin will not know what has happened, and will not know if we have a firewall or the connection just failed. There are also others like LOG, which send a follow-up of the syslog ...
To modify rules, we can edit the iptables file with our preferred text editor, nano, gedit, ... or create scripts with rules (if you want to override them, you can do it by putting a # in front of the line so that it is ignored as a comment) through the console with commands as we will explain it here. In Debian and derivatives you can also use the iptables-save and iptables-restore tools ...
The most extreme policy is to block everything, absolutely all the traffic, but this will leave us isolated, with:
iptables -P INPUT DROP
To accept it all:
iptables -P INPUT ACCEPT
If we want that all outgoing traffic from our team is accepted:
iptables -P OUTPUT ACEPT
La another radical action would be to erase all policies from iptables with:
iptables -F
Let's go to more concrete rulesImagine that you have a web server and therefore the traffic through port 80 must be allowed:
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
And if in addition to the previous rule, we want a team with iptables only be seen by computers on our subnet and that goes unnoticed by an external network:
iptables -A INPUT -p tcp -s 192.168.30.0/24 --dport 80 -j ACCEPT
In the previous line, what we are saying to iptables is to add a rule -A, so that the INPUT inputs, and the TCP protocol, through port 80, are accepted. Now imagine you want me to web browsing is rejected for local machines passing through the machine running iptables:
iptables -t filter -A FORWARD -i eth1 -o eth0 -p tcp --dport 80 DROP
I think the use is simple, taking into account what each parameter of iptables is for, we can add simple rules. You can do all the combinations and rules that we imagine ... In order not to extend myself more, just add one more thing, and that is that if the machine is restarted, the policies created will be deleted. The tables are restarted and will remain as before, therefore, once you have well defined the rules, if you want to make them permanent, you must make them launch from /etc/rc.local or if you have a Debian or derivatives use the tools that are given (iptables-save, iptables-restore and iptables-apply).
This is the first article I see on IPTABLES that, although dense -requires a medium level of knowledge-, GOES DIRECTLY TO THE GRAIN.
I recommend everyone to use it as a "quick reference manual" as it is very well condensed and explained. 8-)
I would like you to talk in a future article about whether the change to systemd in most linux distributions, affects in some way the security of linux in general, and if this change is for the better or worse of the future and linux distributions . I would also like to know what is known about the future of devuan (debian without systemd).
Thank you very much you make very good articles.
Could you make an article explaining the mangle table?
Block only Facebook?