
There is a glut of Linux distributions, although most of them do not contribute anything very useful or new. In this post we are going to deal with one of the exceptions as we will see how to install Kali Linux.
This Debian-based distribution is customized for use in computer security activities, undoubtedly one of the sectors of technological activity that will grow the most in the coming years. The fact that all the tools that Kali Linux includes are and will be free (in addition to being open source) undoubtedly make it an option to consider.
What is a penetration test
Kali Linux is a distribution for running penetration tests.
A penetration test is uA way to find vulnerabilities in a computer system by simulating an attack as would criminals.
The process consists of the following steps
- Planning: In this stage the objectives of the test are defined and in which part of the system it will be carried out. It also determines what types of checks are going to be carried out and the necessary information is collected for them to be successful.
- Exploration: At this stage, an attempt will be made to understand how the application under study will respond to intrusion attempts. This can be done either by analyzing the application's code before running it or while it's running.
- Search and use of weak points: At this stage, different types of computer attacks are tested to detect vulnerabilities and once discovered, try to take advantage of them.
- Access persistence: The goal of this stage is to try to keep unauthorized access undetected for as long as possible.
- Analysis: Once the test is finished, it determines which vulnerabilities were detected, what information was obtained, and how long the attack lasted without being detected.
There are several types of penetration tests. Some of them are:
- External tests: They are directed at those parts of a computer system that can be accessed from the outside. This is the case of mobile applications, websites, email servers or domain names. Attempts will be made to use them to gain access to private data.
- Internal tests: It simulates someone's attack on the system from the inside. Either a person who was actually given access or who has obtained it through phishing techniques.
- Blind test: The evaluators know what the target will be, but not what form the attack will take.
- Double blind tests: Security managers don't even know that a test is taking place.
- Directed tests: Security personnel and testers know the targets and manner of the attack and share information.
How to install Kali Linux
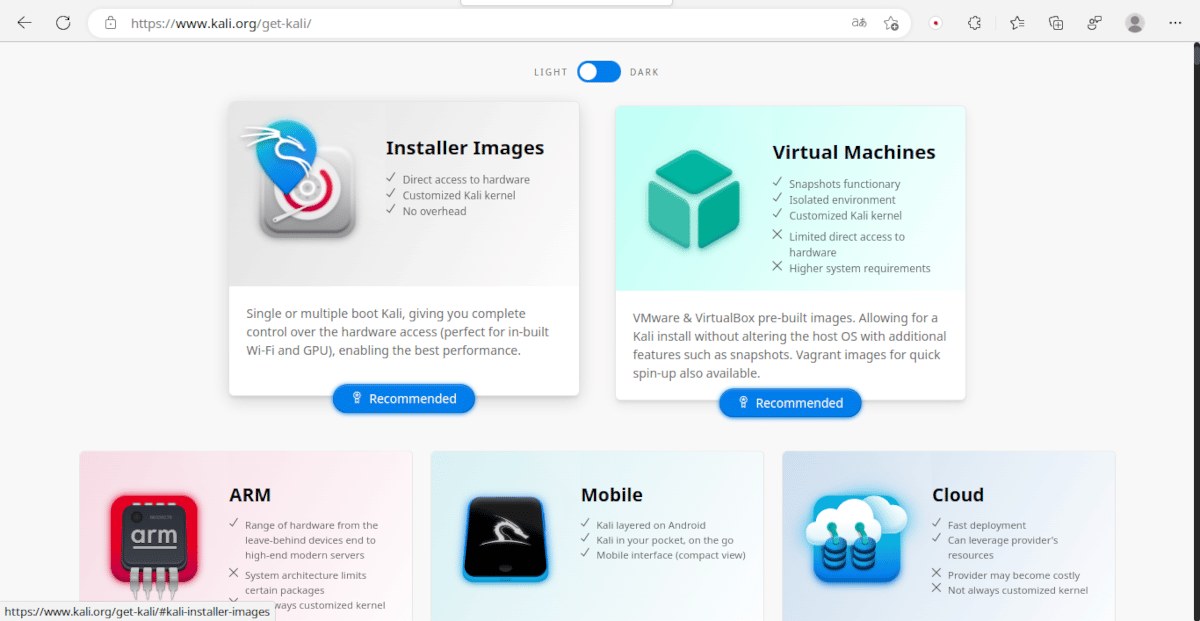
On the Kali Linux website we find different options to download. Some are installable and others support Live mode.
One of the characteristics of Kali Linux is that it can truly be described as cross-platform. as it can run on single board computers like the Raspberry Pi as well as the most powerful of personal computers. That is why when choosing what to download we have several options.
- Installable images: They can be installed without the need for an Internet connection. Unlike other Linux distributions, they cannot be run in live mode (using RAM as if it were a disk). The installable versions are recommended when you don't know which option to choose.
- Network Installable Images: This installation media requires an Internet connection to get the packages to install. This has the advantage that it will install the most current versions, but the disadvantage that it takes longer to install. It requires less capacity support than the previous method and also does not support live mode.
- Live images: It can be run from a dvd or flash drive without installing or using it as installation media, but unlike the previous methods it does not support customization.
- All: As its name indicates, this option includes absolutely the entire range of Kali Linux tools. It requires a large capacity storage medium and is available in two versions: Installable and Live.
Customizations
Installable versions allow us to select the desktop and different package categoriess. The default desktop is XFCE although it is also possible to install others. In the same way, the system can be used with applications without a graphical interface.
Collections of packages (Metapackages) available
Metapackages are categories or collections of packages that can be installed together. during or after the installation: Some of them are:
- kali-desktop-core: Tools required by applications with graphical interface
- kali-desktop-e17: Enlightenment window manager
- kali-desktop-gnome: GNOME desktop
- kali-desktop-i3: i3 window manager
- kali-desktop-kde: KDE desktop
- kali-desktop-lxde: LXDE desktop
- kali-desktop-mate: MATT desk
- kali-desktop-xfce: Xfce desktop
- kali-tools-gpu: Tools that require intensive use of the graphics card
- kali-tools-hardware: hardware hacking tools
- kali-tools-crypto-stego: tools based on cryptography and steganography
- kali-tools-fuzzing: For fuzzing protocols
- kali-tools-802-11:802.11: Tools for wireless networks
- kali-tools-bluetooth: Analysis of Bluetooth devices
- kali-tools-rfid: radio frequency identification tools
- kali-tools-sdr: software defined radio tools
- kali-tools-voip: voice over IP tools
- kali-tools-windows-resources: Tools for the analysis of Windows systems.
Installation procedure
Although there are many tools to create Kali Linux installation media, Ventoy is ideal because we only have to drag the image to the flash drive.
As we said, there are many variants of Kali Linux with different installation methods.. Let's focus on the 64-bit installable image. For other versions and architectures you can consult the official documentation.
The system requirements are:
- 128 MB of RAM (512 MB recommended) and 2 GB of disk space if no graphical interface is used.
- 2 GB of RAM and 20 GB of disk space with desktop and collection of packages by default.
- At least 8 GB of RAM for the most resource-demanding applications.
The steps to follow are:
- Download the Kali Linux image.
- Save the image on the installation flash drive. My recommendation is to use windy.
- In the BIOS options, disable secure boot and select the flash drive as the boot device.
- Restart the system.
- Choose between graphical or text installation mode.
- Select the language.
- Indicate your geographic location.
- Determines the keyboard layout. Spanish from Spain or Latin America.
- The system will try to determine the type of network connection. In the case of a wireless network you will have to enter the corresponding data.
- If you want you can enter a name that identifies the equipment within the network.
- What follows is to enter the account data including full name, username and password.
- The next step is to determine the time zone.
- The step you touch next can be simple or complex. Once the installer shows you the available drives you can tell it to use the entire drive, use empty space or manually set where to install Kali Linux and how much space it will take up.
- Confirm the selection and we decide if we encrypt the disk.
- If the Internet connection requires a proxy, enter the necessary data.
- Choose the categories of packages to install.
- Determine where to install the bootloader.
- When the installation is finished, reboot the system.