In our previous article we had focused on the topic of how to find and download a Linux distribution safely. Before continuing I am going to answer a question that they asked me in the comment form.
The question is whether There are tools (in Windows) that allow us to check the integrity of the image download of a Linux distribution. In this article I will comment on two. The one Microsoft offers and the one you should use.
To better understand the verification procedure we have to first know what a hash is.
When we talk about a cryptographic Hash function (Hash for short) we mean an algorithm that transforms a block of data of any length into a character string of a fixed lengthwhich will vary depending on the algorithm. So for example applying SHA-2
Using the word Diego which has 5 characters we get
8da851d33c85d9eb04377176fc91b7bb9c05981edcfecb64486b36d4
If we use Diego Germán González that has 21 characters we achieved
4aed400d92241480400f9a49e2425e4dcbbf7ca5cf12c05caeeecfae
Which also has 56 characters.
How to check the integrity of the downloaded file
Microsoft provides a tool that can be downloaded. That tool is called File Cheksum Integrity Verifier and it is the kind of cumbersome software to use that the prejudice of the ignorantis usually associated with Linux
File Checksum Integrity Verifier (FCIV) is a checksum calculation application. It is used from the Command Prompt Tool and does not have a graphical interface.
Once downloaded and placed in the correct folder, andThe FCIV program can be used like any other command . FCIV works on Windows 10, 8, 7, Vista, XP, 2000, and most Windows server operating systems.
The File Checksum Integrity Checker used to get a checksum, either MD5 or SHA-1, the two most commonly used cryptographic functions to check the integrity of a file.
The program installation procedure is as follows
- We create a folder called IVF in Windows Explorer.
- We download the program from this link. I couldn't find any Spanish version.
- We double click on the program launcher.
- Click to accept the license (It would not be a bad idea to read it)
- Click on Browse, we choose the folder IVF and click on Accept to extract the files.
- We press on Accept to close the installation window.
- We Click on Start Run and we write cmd.
- We write set path =% path%; path to the folder: \ FCIV so that Windows can run the program.
To check the integrity of a downloaded file we copy it to the FCIV folder and write.
fciv.exe [Comando] <Opción>
As an example we are going to use the XFCE version of the Linux Manjaro distribution. Suppose we have the FCIV folder stored inside the folder Documents of One Drive.
1) We copy the downloaded image to the folder IVF
We know from your website that the XFCE version of Manjaro has the SHA-1 hash
SHA1: c44a2984aa2fada53c1db8c6b919b45152780489
2) We open the command prompt tool and write
set path=%path%;C:\Users\nombre_usuario\OneDriveDocumentos\FCIV
To check the hash we do
fciv.exe C:\Users\nombre de usuario\OneDrive\Documentos\FCIV\manjaro-xfce-20.0.3-200606-linux56.iso -sha1
FCIV is a complicated tool to use and it does not include all the hash cryptography formats used by Linux distributions so it is better to opt for another toolbecause in addition to being open source it has a graphical interface. Is named Quickhash GUI
QuickHash GUI It is cross-platform and is available for Linux, Mac and Windows. Does not require any type of installation and can be run from an external storage device.
The program is downloaded in .zip format and includes versions for 32 and 64 bits. You can delete the one you don't need. Works with MD5, SHA-1, SHA256, SHA512, SHA-3 (256 bit) and Blake2b (256 bit) algorithms. The 32-bit version adds xxHash32 and the 64-bit version xxHash 64
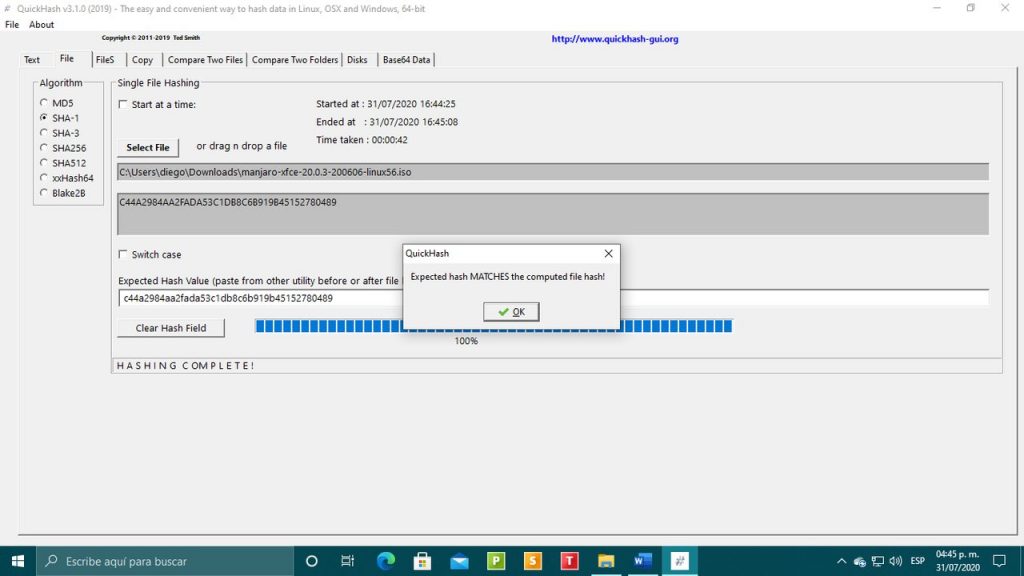
The program has several working modes. The easiest way to do it is:
- Click on the tab Files
- We select the type of algorithm. In our case SHA-1
- We paste the Hash where it says Expected Hash value.
- Load the iso image file by dragging it or clicking on SelectFile.
Quick Hash GUI has an excellent instruction manual that, although it is in English, is perfectly understood.
Different distributions use different algorithms and can post the Hash in different places, but, the usual thing is that it is published next to the download link. If it is not there (as in the case of Linux Mint) it will explain where to find it in the download instructions.
MD5 and SHA Checksum Utility
the fastest and simplest
Now and if one does not use that terrible thing called Windows and uses only Linux, then what should I use? Thanks. Greetings.
The second program that I comment has a version for Linux