
We are very used to talking about software-based security solutions, such as antivirus, firewall, IDS, encryption programs, 2FA, etc. However, for some users, the hardware-based security it is somewhat more in the shade, despite the fact that they could be more powerful and easier to implement solutions in some cases.
That is why I have dedicated this article especially to provide these solutions hardware for security that you can use at home or in the company:
U2F keys

All the U2F keys they are cheap, and it is a kind of hardware-based double authentication system. In order to use this USB device, all you have to do is connect it to your PC as you would a pendrive, only the first time it will generate a random number to generate different hashes that will be used to log in to the linked platforms or services.
When you have to log in to that service, all you have to do is plug the USB key into the port and wait for the browser recognizes it and checks. In this way, other people without having this device will not be able to access your account even if they know the password.
These keys are usually Compatible with the main web browsers, such as Mozilla Firefox, Google Chrome, Opera, etc., as well as some well-known services, such as Google (GMAIL, Docs, Adsense,…), Dropbox, GitHub, Facebook, etc.
If you dare to buy any of these USB keys, here are some recommendations (it is important that they have a FIDO2 certificate):
hardware firewall

Un firewall, or firewalls, is a defense system that blocks unauthorized network access, or allows communications authorized by the user or system administrator. Well, in addition to those based on software, there are also those based on hardware.
These devices can be interesting for companies and servers, being able to configure them in a similar way to a router, from a web interface using the browser. In addition, being placed between the Internet and the router, all the devices connected to said router will be protected, without having to configure each one.
These devices can be found in a more compact form, similar to a router, for the home, or for server racks. Some recommendations are:
- For home:
- For the company:
- For server (rack):
VPN Router and VPN Box

As you know, one VPN (Virtual Private Network) allows you to create an encrypted channel to browse the Internet more securely. In addition, it will prevent your browsing data from being accessible by the ISP, you will be able to access blocked content in your area by changing the IP to that of another country, it will improve your anonymity, etc. Many of these services can be used through client apps, however, these apps should be installed on each of the devices you connect to a network so that they are all under the protection of the VPN.
One solution is to use a vpn router/box that allows you to configure these services (ExpressVPN, NordVPN, VyperVPN, CyberGhost, Surfshark, IPVanish...) and thus all the devices you connect to it will be protected (mobile devices, smart TVs, consoles, PCs, IoT, etc.). Even if there was no client app for that platform.
Some router recommendations good to use with VPN:
Shellfire also has the vpn box, which are automatic and auto-configured to make things easier for non-technical users:
encryption hardware

El encryption it is usually a somewhat "heavy" task for the hardware. However, there are hardware encryption cards or devices that assist the software. These systems implement a dedicated processor for this, which can be an advantage. There are some based on ARM chips, on x86, also in PCI card format, USB keys to encrypt data, etc.
Some of the most practical solutions to have your encrypted data are USB keys and external hard drives they have encryption system built-in. here you can find some recommendations on the table:
You also have Hardware Encrypted NAS included, to have your "cloud" private and secure, such as:
PKI token hardware

The PKI tokens they are hardware devices that store private keys and digital certificates securely. When you need to encrypt, decrypt, or sign for some type of service, procedure, etc., you can use these devices safely.
In the market you can find several of these solutions, Such as Thales group, macro securitythose of microcosm, etc.
You also have at your disposal some SmartCard or smart card readers, as well as for the electronic DNI to perform online transactions. Some of these recommended devices are:
SSL/TLS Accelerator
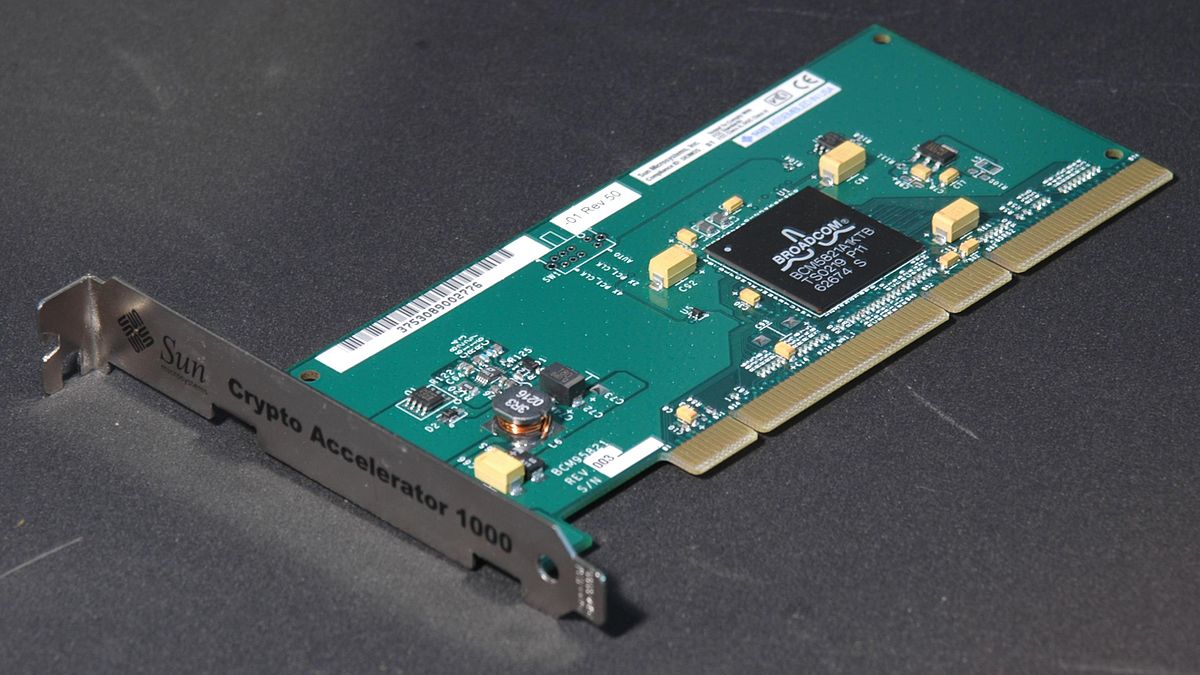
The hardware SSL/TSL accelerators They are devices that also contribute to security, and that you can find in various formats, such as PCI expansion cards, in addition to being installed in racks. A way to offload the CPU from this work, since this other component will be dedicated to it. However, these systems are not used in the home or small business, but on servers.
Secure hardware payment system

These secure payment systems by hardware they do not make much sense at home either, but they do for some organizations, companies, etc. These HSM systems are security-enhancing and tamper-resistant devices that can be used in the retail banking industry. Thus, it provides high levels of protection for encryption keys, customer PINs used in magnetic stripe cards and EMV chip (or similar) issuances, etc. Some providers of this type of solutions are Thales, PayCore, services such as MyHMS, etc.
Wallet or purse for cryptocurrencies

Wallet, or portfolio, wallet, virtual wallet, or whatever you want to call it, is a system to store and manage your assets in cryptocurrencies. It can be implemented by software or also by hardware, designed exclusively to store the public and private keys of your cryptocurrencies.
Some purchase recommendations are:
Biometric sensors

There are several types of biometric sensor to improve hardware security, and that can replace access methods with conventional credentials (username and password) by the recognition of unique biometric parameters in each person. For example, there are some like:
- Fingerprint sensors.
- Facial recognition.
- Iris recognition.
- Speech recognition.
- Hand geometry.
- Signature verification.
They can be used for various applications, from accessing a service or logging in, to opening doors, etc. In other words, they can not only help you improve digital security, but also at a physical or perimeter level. Some devices that may interest you are:
Kensington lock and similar

And the famous kensington lock It is a security connector that can be inserted into a small hole included in some models of laptops and whose purpose is to prevent theft of these devices. It is used to anchor a lock and was designed and manufactured by Kensington Computer Products. Currently, there are other brands that offer similar solutions.
Some purchase recommendations are:
Others

Also exist many other solutions to improve hardware security, some not without controversy, others very cheap and practical. From the usual covers for the front cameras (the webcam of a laptop, AIO, mobile phones), so that they do not monitor you without your consent, to false data generators such as the charger Mud.











































