
Some days ago Google announced the opening of the Sandboxed API project, who Allows you to automate the sandbox creation process for isolated execution of arbitrary libraries in C and C ++.
Isolating your code from libraries allows to protect against possible attacks on the handles provided by the libraries, creating an additional barrier in case there are vulnerabilities in your code that can be exploited through manipulations with the external data that enters the library. The code is open under the Apache 2.0 license.
The isolationor it is done using within the Sandbox2 runtime, in which the namespaces, cgroups, and seccomp-bpf are used.
The code delivered to the sandbox that runs in a separate process, for which access to system calls and resources, as well as files and network connections, is limited.
Processes gain access only to system capabilities that are directly required to execute isolated code.
Sandbox2 defines the components to run the processor, apply the isolation rules and support the subsequent execution.
sandbox2 it can be used separately from the Sandbox API to isolate not only libraries, but also arbitrary processes.
In addition to increasing protection, a positive point in the elimination of the code in separate processes is the possibility of a separate regulation of the limits on the memory consumption of the library and the CPU, as well as the protection against failures: a failure in the library does not cause the entire application to crash.
About Sandboxed API
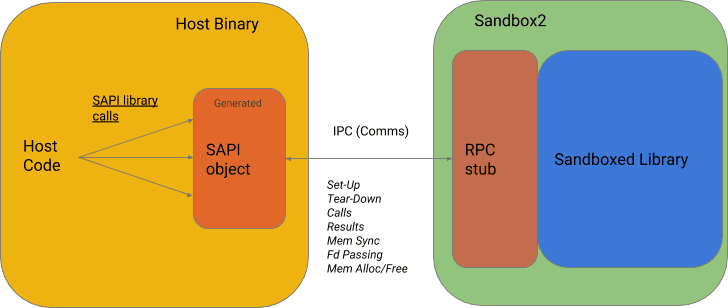
Sandboxed API is a plugin for Sandbox2 which simplifies the transport of existing libraries to run in isolated mode.
API sandboxing provides an intermediate software interface that allows you to run the library code in a sandbox environmentas well as organizing a call to a library in a sandbox environment and ensuring the delivery of the library results to the main program.
Se accesses the isolated library through a specialized RPC based on the ProtoBuffs protocol.
A library developers are offered a set of options that allow access to variables, file descriptors, buffers and library functions isolated from the base application, including tools for automatic and controlled memory synchronization for sharing arrays and structures.
When a software library that analyzes such data is complex enough, it can fall victim to certain types of security vulnerabilities: memory corruption errors or other types of problems related to the analysis logic (for example, path traversal problems). ). Those vulnerabilities can have serious security implications.
In addition, An API is provided to monitor the operation of isolated processes and restart them in case of failures.
For the isolated library, annotations code of the isolated functions is automatically generated for the Bazel assembly system and the program interface (SAPI) for the interaction between the basic and isolated processes.
The developer must also create a header file with isolation rules that define all allowed system calls and operations (read, write, open files, access to time, the ability to install signal handlers, support for memory allocation via malloc, etc.).
The files and directories that the library should have access to are determined separately.
Installation
Currently, the project is available only for Linux, but in the future they promise to add support for macOS and BSD systems, and in the long term, and for Windows. Yes you want to install sandboxed api you can follow the given instructions this link.
Of the plans, it is also noted the ability to isolate libraries in languages other than C and C ++, additional runtime support for isolation (eg based on hardware virtualization) and the ability to use CMake and other assembly systems (support is now limited to the Bazel build system).
Source: https://security.googleblog.com