
In these times with so many vulnerabilities in both software and hardware where these problems can be exploited to have remote access to certain machines and even make a remote or local privilege escalation on the victim machine, it is important to carry out all the necessary security procedures and protocols that we know or that we have at our disposal to keep our data safe. And if you work with sensitive data or have a company whose clients give you information, with much more reason.
We have already repeated by active and passive that you must keep the system updated, avoid being online when possible, the most sensitive data should be stored in a removable local storage device, in order to avoid that the information is always available on the machine that it can be vulnerable, and of course always make regular backups. Besides that, I recommend you encrypt the content of your files or make complete encryption of your partitions so that the data is not accessible without the password to decrypt it, even if you have access to the machine ...
What is encryption?
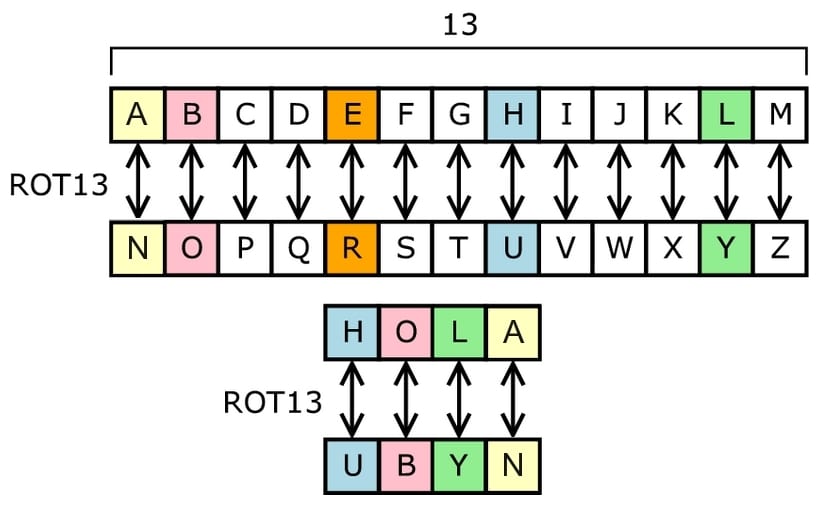
Source: Wikipedia
On many websites and tutorials you will find the word encrypt and decrypt to refer to the encryption and decryption of computer data. But, if you did not know, I will mention it to you, these terms have some controversy, although it seems that they are quite accepted and widespread due to how frequent they are, even among professionals in the sector. The confusion comes from cryptography or the science of concealment, and more specifically the English term "encrypt" which comes from a neologism directly taken from the Greek krypto, and which has been translated directly into Spanish as encrypt.
On the other hand, in Spanish it seems that you are saying "put in a crypt" something "take something out of a crypt". However, if we analyze the Greek where all this comes from, which is "krypto" means to hide. However, you can use the term that you like the most ... in fact the RAE has ended up accepting it as synonymous with encrypt. Personally, I prefer not to pay too much attention to these corrections and prefer to use both synonymously and leave "the science or art of concealment" to steganography as a broader term.
Conclusion, when we talk about encryption or encryption of data or messages we are referring to a procedure to transform information to protect it in some way. The most common is to use some kind of character swapping or algorithm so that sensitive information is transformed into a meaningless string of letters, numbers and symbols. While the decryption or decryption procedure is the reverse procedure, in which that nonsense information is transformed into something understandable to the machine or human.
A Little History

This art of making it difficult for third parties by transforming information it's not something new, It has been done for millennia, specifically more than 2500 years ago. From the Egyptians who used hieroglyphs to the times of Imperial Rome with the Caesar code, so called because Julius Caesar (100 BC - 44 BC) used it to encrypt the messages he sent to his troops so that if these messages fell into enemy hands, they would not could understand them and did not gain military advantage from them.
In more modern times we also have the example of the nazi enigma machine, which used a series of cylinders to encode or encrypt the information that the German commanders passed to the troops and thus prevent the enemies from knowing the movements that Hitler's soldiers were going to make. In fact, it was these encrypted messages that fueled computing in the United States and England, as the first computing machines were created to attempt to decipher these complex messages.
As you know, there are several encryption types, such as symmetric and asymmetric, and you will see how GnuGP or GPG can work in both modes:
- Symmetric encryption- When a single key is used to encrypt and decrypt messages, files, etc. Within this type of encryption we can find and use various encryption algorithms such as AES, DES, 3DES, etc.
- Asymmetric encryption: in this case two keys are used, one public and one private. The public is used to encrypt and the private to decrypt. Within this type of encryption we also have various encryption algorithms, such as RSA, ElGramal, etc.
The key what it achieves is that by means of this algorithm, the information is transformed and it is impossible to obtain without having said key to decipher it ...
Background: PGP
Many confuse PGP with GPG and it is not the same. PGP stands for Pretty Good Privacy and which describes a program developed by Phil Zimmermann to encrypt, decrypt and sign data to protect it. It appeared in 1991 and was a fairly popular program that combined symmetric and asymmetric encryption techniques to secure information.
But PGP was a somewhat problematic software because of the licenses of some algorithms, they were not open and in PGP Inc. they were quite concerned about the patents that made them take another direction. Zimmermann understood that a free standard for PGP was essential due to the importance that PGP had taken at the time, so they proposed a standard called OpenPGP, something that would become the germ of GPG.
What is GPG?
GnuPG or GPG (GNU Privacy Guard) is a software developed by the FSF (Free Software Foundation) to implement an OpenPGP compatibility program. With it you can encrypt and decrypt plain text messages, files, and make digital signatures to secure the content that we transfer by email or any other network service. Also, GPG is free and free under the GPL license.
You can work from the console or terminal by using commands or there are also some GUIs that can be installed or programs that help to work with GPG but from a somewhat more friendly and intuitive interface for those who do not like the shell so much and prefer to do it from the desktop environment. Some of these programs will surely sound familiar to you, since they are quite popular on Linux distros, as is the case with Seahorse.
GnuPG tutorial:
As I say it is not the only alternative we have in our distro to encrypt and decrypt, since there are many other possibilities beyond GPG, such as OpenPGP itself. In fact we have already dedicated some titles to other alternatives such as ecryptfs to encrypt directories and partitions, cryptmount, ash, etc. Also, if you decide to use GPG through any of the available GUIs, you are also free to do so, but here I am going to describe the procedure to quickly encrypt and decrypt files using commands from the terminal.
Encrypt files with GPG:
To encrypt files with GPG from the console of your GNU / Linux distro, the first thing you should do is have installed GPG in your distro, for this you can use any package management tool since the pupularity of this tool makes it available in all repositories. For example, on Debian and derivatives you can try with:
sudo apt-get install gnupg2
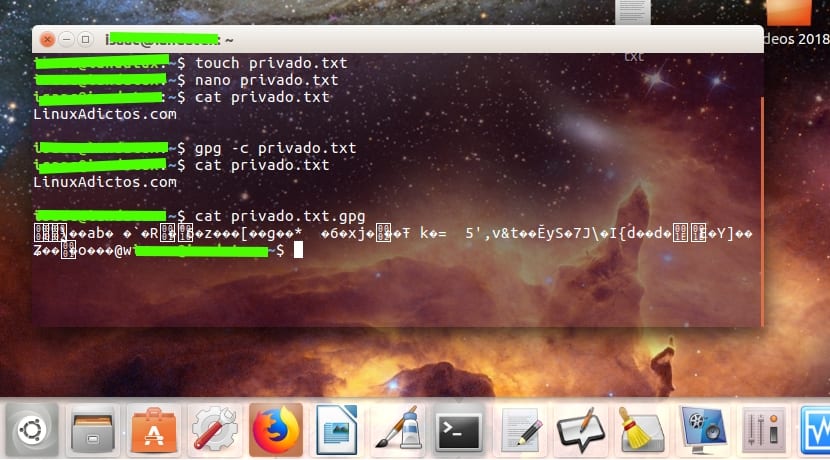
Once installed you can start using it. For example, imagine that you have a text file that you want to encrypt. We are going to call this file private.txt in which I am going to enter the text LinuxAdictos.com and to encrypt it:
gpg -c privado.txt
And now We would already have it encrypted after entering the passphrase that will ask us, that is, the encryption key (it asks us again to confirm and see that we have not made a mistake when typing it, since if you put another key and do not remember it or get confused, then you will not be able to decrypt it). Eye! Be careful because the encrypted file will not be called private.txt, but instead a .gpg extension is added to differentiate it from the other, so do not get confused when sending the initial file, since it will not be protected ...
Decrypt files with GPG:
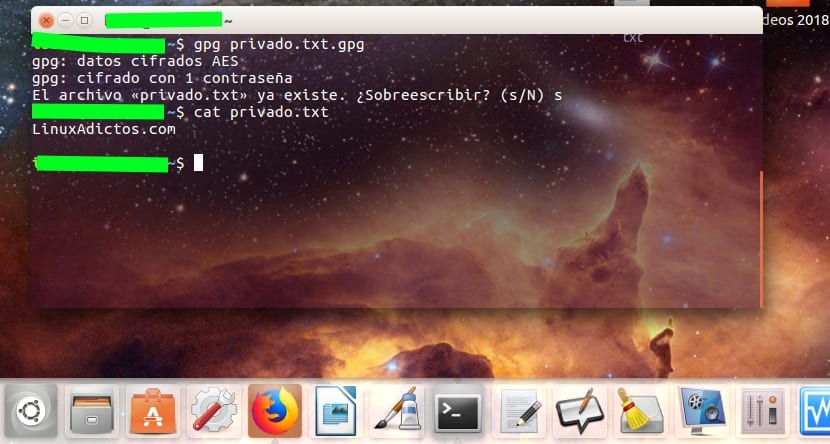
Now, you can delete the original if you want and just leave the private file.txt.gpg that appears encrypted and you cannot understand at all the message that we have included inside it, which remembers that it is the name of this blog. Well if we want decrypt the message and recover our human-readable and understandable file, it will be enough for us to remember the password that we put before when it asks us after executing the following command:
gpg privado.txt.gpg
And now after enter the password we will have the file again as before encrypting it. By the way, as you can see in the screenshot I made, it can be seen that the GPG program has used the AES128 encryption algorithm by default, since we have not specified any other alternative when we encrypt the file. But if you want to modify the type of algorithm you can through the option –Cypher-something followed by the type of algorithm you want from among those that GPG supports (you can see more information in man gpg). And if you want to know the supported algorithms, you can see them with:
gpg --version
And the algorithm list plus information about the GPG version, etc.
Do not forget to leave your comments, questions and suggestions ... I hope this tutorial will be of great help to you.
The only downside I see is that with this system, the file NOT encrypted remains "available". In my case, I need the initial file to be safely deleted and / or converted to another encryption, without leaving any remains on the client computer.
There is an application based on CCRYPT with a graphical interface (qt5) or with a terminal, it is called Qccrypt for debian / ubuntu.
A greeting!
I did a test and with the command to encrypt I had no problem but when using the command to decrypt it turns out that it did not ask me for the password and the original file appeared again. What happened?
Troszkę późno, ale odszyfrowanie pwidłowo, powinno wyglądać tak: gpg -o (nazwa pliku jaki chcemy otrzymać po odszyfrowaniu) -d (nazwa zaszyfrowanego pliku.gpg)
In Spanish: "A bit late, but decrypting correctly, it should look like this: gpg-o (filename we want to receive after decryption) -d (encrypted filename.gpg)".