
Recently the team of Docker issued a security advisory to announce unauthorized access to a Docker Hub database by an unidentified person. The Docker team became aware of the intrusion that lasted for only a short period on April 25, 2019.
The Docker Hub database exposed sensitive information for approximately 190,000 users, including hashed usernames and passwords, as well as tokens for the GitHub and Bitbucket repositories whose use not recommended by a third party could compromise the integrity of the code repositories.
According to Docker's opinion, the information in the database included access tokens for the GitHub and Bitbucket repositories that are used for automatic code compilation in Docker Hub, as well as usernames and passwords a small percentage users: 190,000 user accounts They represent less than 5% of Docker Hub users.
In fact, GitHub and Bitbucket access keys stored in Docker Hub allow developers to modify their project code and automatically compile the image to Docker Hub.
The applications of those affected could be modified
The potential risk for the 190,000 users whose accounts were exposed is that if an attacker gains access to their access tokens, you could get access to their private code repository that they could modify based on permissions stored in the token.
However, if the code is changed for the wrong reasons and compromised images have been implemented, this could lead to serious supply chain attacksas Docker Hub images are commonly used in server applications and configurations.
In your security advisory posted Friday night, Docker said that it had already revoked all tokens and on-screen access keys.
Docker also said it improves its overall security processes and reviews its policies. He also announced that the new monitoring tools are now in place.
However, it is important that developers, who have used the automatic build of Docker Hub, check your project repositories for unauthorized access.
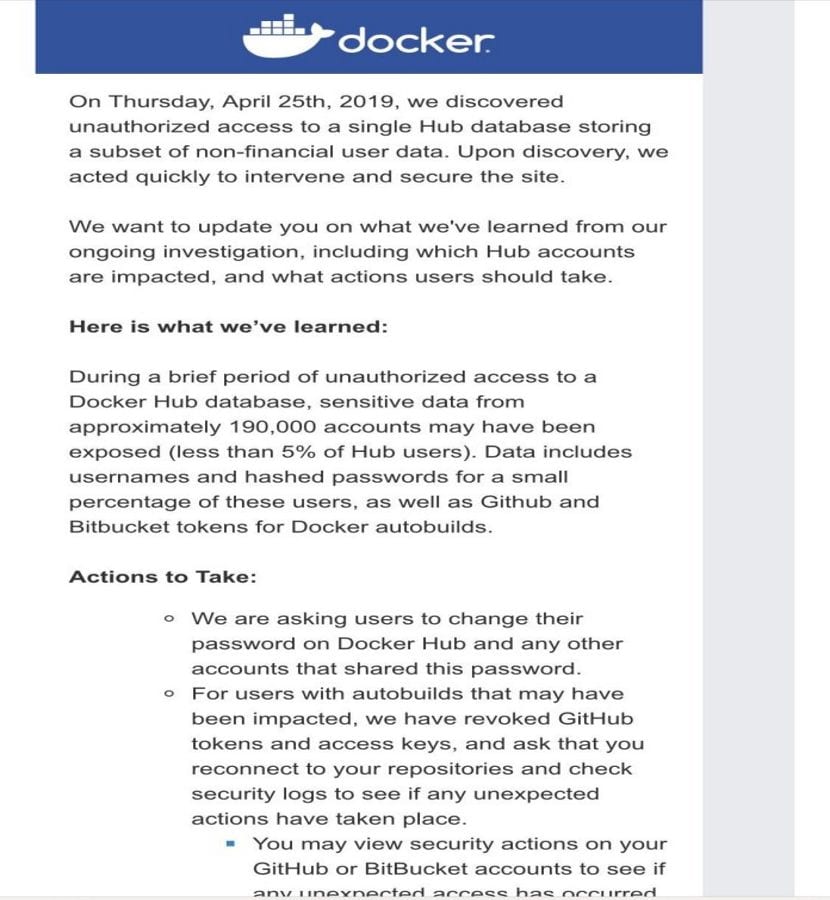
Here is the security advisory posted by Docker on Friday night:
On Thursday, April 25, 2019, we discovered unauthorized access to a single Hub database that stores a subset of non-user data. financial Upon discovery, we act quickly to intervene and secure the site.
We want to let you know what we've learned from our ongoing investigation, including which Docker Hub accounts are affected and what actions users need to take.
This is what we have learned:
During a short period of unauthorized access to a Docker Hub database, sensitive data from approximately 190,000 accounts (less than 5% of Hub users) may have been exposed.
The data includes the hashed usernames and passwords of a small percentage of these users, as well as the Github and Bitbucket tokens for automatic Docker builds.
Action to take:
We ask users to change their password in Docker Hub and any other account that shares this password.
For users with auto-build servers that may have been affected, we have revoked the access keys and tokens from GitHub and you are prompted to reconnect to your repositories and check the security logs to see if there is any action. Unforeseen events occurred.
You can check the security actions on your GitHub or BitBucket accounts to see if there has been any unexpected access in the last 24 hours.
This may affect your current builds from our automated build service. You may need to disconnect and reconnect your source provider Github and Bitbucket like described in the link below.