
Surely you know a multitude of tools and alternatives to perform backup In GNU / Linux environments, from the typical apps that are pre-installed in some distros such as Dejavù in Ubuntu, or others like Timeshift, and even bash scripts that you have been able to do at some point in your life, you have downloaded from a web or you have made copies directly using the dd command, etc.
In this tutorial we introduce you to a new tool called CYA which is the acronym for Cover Your AssI mean, literally cover your ass. As you can deduce from its name, this tool for Bash in Linux allows you to save your ass when something goes wrong in your operating system and allows you to create a complete snapshot to be able to restore it so that the problem does not become a drama, especially if we have information sensitive, business, or we have a complex architecture built that we do not want to lose.
The importance of backing up

Una backup or backup or backup It is a copy of the original data that is made with the aim of having an alternative means to go to in case the data is lost, corrupted or something happens to the hardware or system that leaves it out of service. In that case, we will not lose anything, as we will have an exact copy of which to throw away in an emergency. They can be done without compression, although on many occasions they can be done on hard drives, optical media, in the cloud, etc., even with compression, although that will require more hardware resources and time to perform compression and decompression, in addition to Sometimes if the compressed file gets corrupted it could cancel the backup ...
Backups seem obvious but that many users and worse, companies, forget perform periodically. And when problems come, everyone remembers them, but it is too late. Especially now with ransomware threats, it is important not to neglect backup copies, since this type of malware encrypts hard drives and keeps data inaccessible unless you pay the ransom that some cybercriminals ask for to provide you with the key that can decrypt it. . The money they usually ask for is quite high and increases according to the importance of the affected victim, for example if it is a company with very sensitive data, the figure they will ask for will be higher. On the other hand, if we have made backup copies, we would avoid this problem in a simple way.
What is a Snapshot?

Un snapshot or instant copy It is a somewhat special case of backup, since they go beyond copying certain data from the storage medium, and copy the state of a system at a certain time. Hence its name, since it is as if we took a snapshot of how the operating system is in a moment and through the appropriate restoration tool to be able to recover that same configuration state and real state.
From this it follows that the main difference from a snapshot and a simple backup is that the first is oriented to the state of the OS and the second is more focused on the integrity of the data. Many backup programs also offer the option of taking a snapshot of the operating system, as is the case with the CYA tool that we present to you to make copies or snapshots of your host system, not the guest, although as I explain in the next paragraph it's possible…
Muchos hypervisors or virtualization systems They also offer the ability to create snapshots of virtualized environments, something very practical to make copies of the virtual machines that we have in operation. I especially like it when I have some type of server mounted on a VM, since once I have installed all the necessary packages and have them configured and running, I take a snapshot so that in case something goes wrong, I can recover the system from that same state in which everything works OK at any time.
Use CYA on Linux
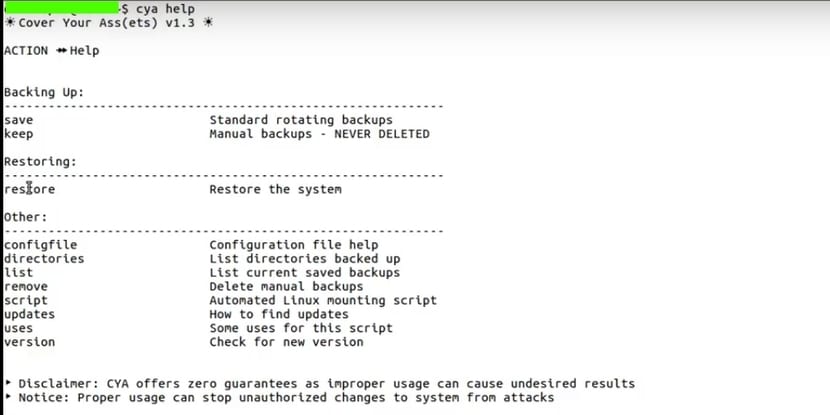
If you do not know CYA I present it to you, although you can get a lot of information from it in the official website from its developers. As I said before, it allows us to take a snapshot of our system from Bash, since it is a tool for open source for this shell and whose source code you can find on the GitHub website. It not only works on Linux, but also on any other Unix operating system with this shell like FreeBSD, OpenBSD, Solaris, etc.
CYA in principle works under any filesystem, since it is a tool totally independent of FS and it is not limited to the typical native FSs of these * nix systems such as ext2, ext3, ext4, UFS, XFS, ZFS, btrfs, etc., something that is appreciated when we work with several of these systems in our OS, since some Apps to make this type of copies do depend on or are limited to certain FS.
With CYA we can easily automate the copies of our system and manage them easily to keep you always protected against any threat, be it malware, bugs in the software itself, problems with storage media, or administrative errors.
For using CYA you can follow these simple steps:
- Download CYA ZIP file from the link I left you earlier.
- Unzip and give it permissions 755 or 700 to the file called cya:
chmod 700 cya
- If you want you can copy cya in the path / home / your_name / bin / or in / usr / local / bin to be able to execute it simply by invoking its name and not having to go to the directory where it is located every time ...
- Now you can comment to run it (to get the recovery script called recovery.sh and that you should save on a USB or somewhere safe, while the second command is helpful for the options you can use):
cya script cya help
- To create a Backup rolling standard you can run:
cya save
- Instead, if you created the recovery.sh script by running cya script, you can recover the system from any of the copies that you have made by executing the script:
./recovery.sh
Do not forget to leave your comments, doubts, suggestions, etc. Now you have no excuse for not maintaining a good copy policy for your system ...