BLAKE3 es a cryptographic hash function which it is characterized by being much faster than MD5, SHA-1, SHA-2, SHA-3 and BLAKE2, plus it is more secure, unlike MD5 and SHA-1. And safe against length extension, unlike SHA-2.
It is highly parallelizable across any number of threads and SIMD lanes, because it is a Merkle tree on the inside and has a variant-free algorithm, which is fast on x86-64 and also on smaller architectures.
BLAKE3 relies on an optimized instance of the established hash function BLAKE2 and in the original Bao tree mode. Specifications and design justification are available on BLAKE3 paper. The default output size is 256 bits.
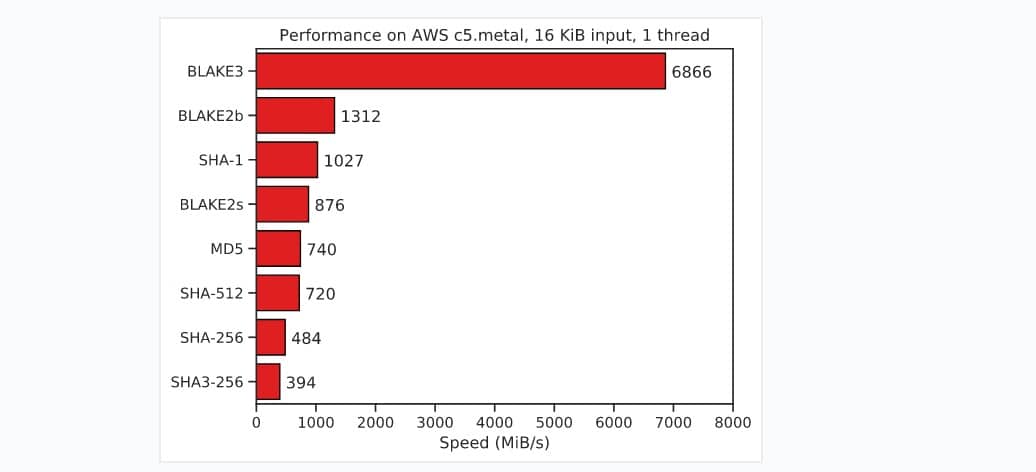
In the hash generation test for a 16 KB file, BLAKE3 with a 256-bit key outperforms SHA3-256 by 17 times, SHA-256 by 14 times, SHA-512 9 times, SHA-1 6 times and BLAKE2b 5 times.
This is a significant gap that remains even when processing large amounts of data, for example BLAKE3 turned out to be 8 times faster than SHA-256 when calculating a hash for 1GB of random data.
The performance improvement was achieved by reducing the number of rounds from 10 to 7 and hashing blocks separately into 1 KB chunks. According to the creators, they found compelling mathematical proof that you can get by with 7 rounds instead of 10 while maintaining the same level of reliability.
At the same time, some researchers express doubts, believing that even if currently 7 rounds are sufficient to counter all known attacks in hashes, then 3 additional rounds may be useful if new attacks are detected in the future.
About BLAKE3
The hash function is designed for applications such as file integrity verification, message authentication and data generation for cryptographic digital signatures. BLAKE3 is not designed for hashing passwords as it aims to compute hashes as quickly as possible (for passwords, it is recommended to use the slow hash and escrypt, bcrypt, scrypt, or Argon2 functions).
The hash function in question is insensitive to the size of the data being processed and is protected against collision hunting and preimage attacks.
The algorithm was developed by renowned cryptographers and continues development of the BLAKE2 algorithm and uses the Bao mechanism to encode the blockchain tree. Unlike BLAKE2 (BLAKE2b, BLAKE2s), BLAKE3 offers a single algorithm for all platforms which is not tied to bit width and hash size.
With regards to block splitting, in BLAKE3 the stream is split into 1 KB chunks and each hash fragment independently. A large hash is formed on the basis of hashes of pieces based on the Merkle binary tree.
This separation allows solving the problem of parallelizing data processing when calculating a hash; for example, you can use 4-wire SIMD instructions to simultaneously compute 4-block hashes. Traditional SHA- * hash functions process data sequentially.
Other BLAKE3 features are:
- Application in PRF, MAC, KDF, XOF modes and as normal hash;
- An algorithm for all architectures, fast on both x86-64 systems and 32-bit ARM processors.
Regarding the main differences between BLAKE3 and BLAKE2:
- Using a binary tree structure to achieve unlimited parallelism in the hash calculation.
- Reducing the number of rounds from 10 to 7.
- Three modes of operation: Hash, Keyed Hash (HMAC), and Key Generation (KDF).
- There is no additional overhead when hashing a key due to the use of the area previously occupied by the key's parameter block.
- Built-in mechanism to work in the form of Extensible Output Function (XOF) that allows it
- parallelization and positioning (search).
Finally if you are interested in knowing more about it, you can check the details In the following link.