The last few months don't seem to have been very good for the Norton computer security suite. Already we had informed of the unfortunate inclusion of cryptocurrency software in its security suite. Now they attack the Norton password manager.
A password manager is an essential computer security tool since, By preventing us from having to remember them, it allows us to have different passwords for different services. For one of them to be attacked is like breaking into the police department.
Attack on Norton's password manager
NortonLifeLock (which merged with Avast is part of a company called Gen Digital) sent a communication to the Vermont General Office announcing the detection, in the middle of last month, of what it described as "An unusually high volume of failed logins to our customer accounts."
According to the company:
We determined that, beginning around December 1, 2022, an unauthorized third party had used a list of usernames and passwords obtained from another source, such as the dark web, to attempt to log into Norton customer accounts. Our own systems were not compromised.
As stated by a spokesperson for Gen Digital, Norton's parent company, the most pessimistic scenario would be 8000 accounts compromised through a maneuver known as a "Credential Stuffing Attack". Gen Digital boasts of having prevented 925000 attacks by warning account holders with multiple failed login attempts to change the master password and implement additional security measures.
What is a credential stuffing attack?
The credential stuffing attack consists of testing the username and password of one service in another. The cybercriminal illegally obtains the list of users and passwords from one service and tests them on other services, betting on the laziness or lack of memory of those users that prevents them from creating a new one for each new place they create an account. In general these checks are done by bots.
Despite the belief imposed by Hollywood, the best computer criminals are more skilled as psychologists than as technology users. This type of attack is based on the knowledge that 85% of users reuse their passwords.
In statistical terms, the effectiveness is very low, only 1 in 1000 accounts can be breached. Now, if we multiply this by the millions of user accounts on the web, and that many of these accounts contain sensitive data such as credit card numbers or access credentials to strategic sites, the damage can be incalculable.
How to protect yourself from credential stuffing attack
Traditional security measures such as blocking IPs that fail multiple attempts or delaying access are no longer effective. The bots simulate income from different devices and different locations.
Some ways to prevent this attack are:
- Two-step authentication: This involves using a device or app-provided code that certifies that the legitimate user is the one attempting to log in. In the first case, a notice is sent by text message or email to the user to confirm her identity. In the second, the application generates a code (Based on random factors) that must be typed in the login form of the service to which you want to access.
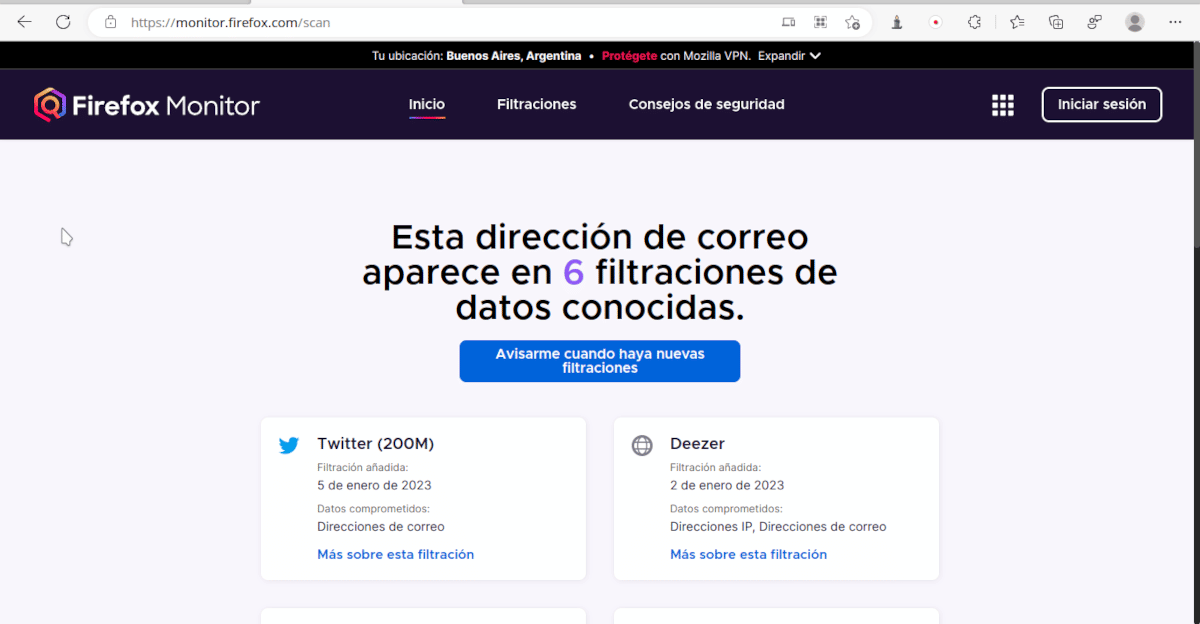
- Firefox Monitor: Es a web from the Mozilla Foundation that warns if an email address is part of an online data breach. The screenshot at the top of this article is what I got from entering my primary email address.
- Password manager: It is the fundamental protection tool for this type of attack since it allows you to assign a new one to each service without having to memorize them. It can be found as a browser extension, in your distribution's repositories, or in your mobile device's app store. Of course, protect it with a master password that you have not used before