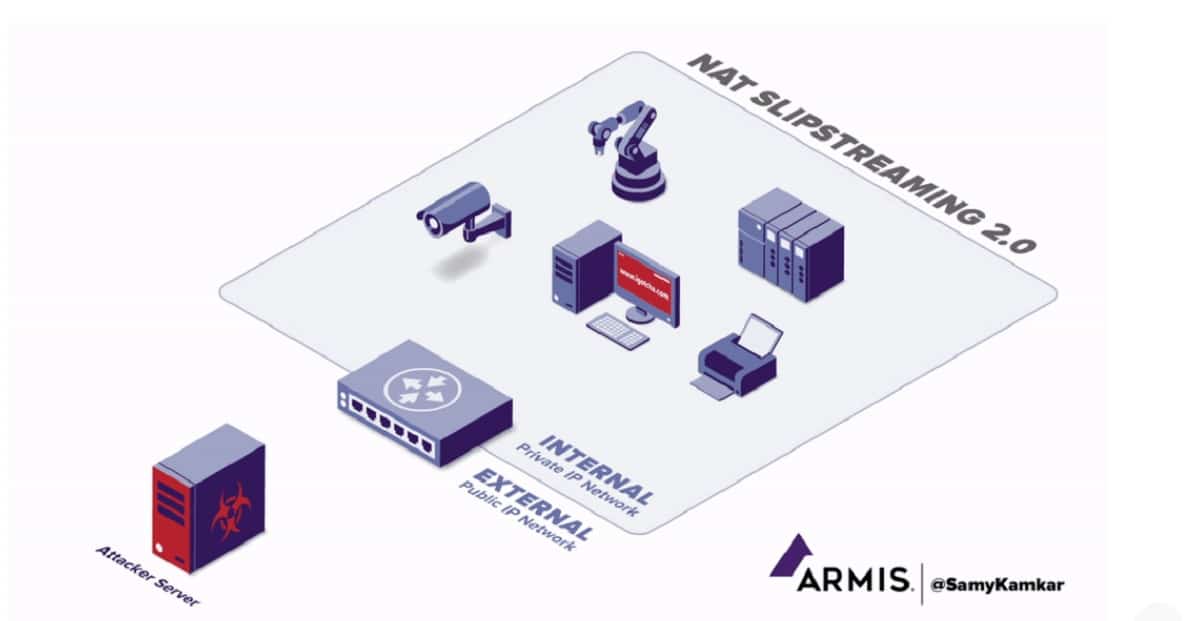
A new variant of the NAT slipstreaming attack was unveiled, which allows establishing a network connection from the attacker's server to any UDP or TCP port on the user's system that opened the web page prepared by the attacker in the browser.
El ataque allows the attacker to send any data to any user port, regardless of the use of the victim's internal address range in the victim's system, access to the network from which it is closed directly and is possible only through an address translator.
The operating principle of the new variant by NAT slipstreaming attack (CVE-2021-23961, CVE-2020-16043) ands identical to the original method, the differences are reduced to the use of other protocols, which are processed by the ALG (Application Level Gateways).
In the first variant of the attack, to fool the ALG, manipulation of the SIP protocol was used, which uses several network ports (one for data and one for control). The second option allows similar manipulations with the VoIP H.323 protocol, which uses TCP port 1720.
Also, the second version proposes a technique to bypass the blacklist of ports that are unacceptable for use with the TURN (Traversal Using Relays around NAT) protocol, which is used in WebRTC to communicate between two hosts behind different NATs.
TURN connections in WebRTC can be established through browsers not only for UDP, but also via TCP and go to any network TCP port.
This feature allows the NAT slipstreaming attack to be applied not only to H.323, but also to any other combined protocolsuch as FTP and IRC, which are included in the list of ports that are not allowed to access via HTTP, but are not included in the list of prohibited ports for TURN.
The method also allows bypassing added protection to browsers against the first NAT slipstreaming attack, based on denying HTTP requests to port 5060 (SIP).
The problem has already been fixed in recent versions of Firefox 85, Chrome 87.0.4280.141, Edge 87.0.664.75, and Safari 14.0.3.
In addition to the network ports associated with the H.323 protocol, browsers are also blocked from sending HTTP, HTTPS, and FTP requests to TCP ports 69, 137, 161, and 6566.
In the Linux kernel, the functionality of the conntrack ALG module in netfilter is disabled by default since version 4.14, ie By default, address translators based on new Linux kernels are not affected by the problem.
For example, OpenWRT is not affected by the problem even when installing packages with ALG modules. At the same time, the vulnerability manifests itself in the VyOS distribution, which uses the Linux 4.14 kernel, but the nf_conntrack_helper flag is explicitly enabled, which triggers ALG for FTP and H.323.
The problem too affects many consumer routers that ship with older Linux kernels or that change the ALG settings. Attack capability has also been confirmed for Fortinet (FG64, 60E), Cisco (csr1000, ASA), and HPE (vsr1000) hardware-based enterprise firewalls and address translators.
As a reminder, to carry out a NAT slipstreaming attack, it is sufficient for the victim to launch the JavaScript code prepared by the attacker, for example by opening a page on the attacker's website or viewing a malicious ad insert on a website. legitimate.
The attack consists of three stages:
- In the first stage, the attacker obtains information about the user's internal address, which can be determined by WebRTC or, if WebRTC is disabled, by brute force attacks with measurement of response time when requesting a hidden image.
- In the second stage, the packet fragmentation parameters are determined, for which the JavaScript code executed in the victim's browser generates a large HTTP POST request (which does not fit in a packet) to the attacker's server, using a non-standard network port number to start the configuration of the segmentation parameters of TCP and MTU size in the TCP victim's stack.
- In the third stage, JavaScript code generates and sends a specially selected HTTP request (or TURN for UDP) to TCP port 1720 (H.323) of the attacking server, which, after fragmentation, will split into two packets: the first includes HTTP Headers and a part of the data, and the second forms a packet Valid H.323, which contains the internal IP of the victim.
Source: https://www.armis.com