
Recientemente some people noticed a strange change in the source code of the Linux kernel, for when reviewing the kernel code on GitHub They noticed that changes made by third parties (those who cloned or forked this one) were appearing strangely in the main repository.
This caught the attention of some on the GitHub interface as an interesting feature was revealed which allows you to present any third-party changes as a change already included in the main project.
For example, today on social networks a reference to a change in the official mirror of the main Linux kernel repository began to spread, indicating the replacement of a back door in the HID-Samsung driver.
A GitHub quirk alarmed kernel developers
Faced with this conflict some began to check the kernel code especially in the Samsung driver in addition to trying to verify if the security of the kernel had been compromised.
An analysis of the situation showed that GitHub, to optimize storage and minimize duplication of data on its servers, stores all objects from the main repository and the forks associated with it, logically sharing ownership of commits.
With which This storage allows anyone who is browsing within the code to see any confirmation from any fork in any associated repository, explicitly indicating its hash in the URL.
For example, in the case of a backdoor demo, one of the users created a fork of the main Linux kernel repository in the GitHub interface, then added a commit with backdoor-like code to his fork.
After that, it formed a link in which the SHA1 identifier of the external change was substituted in the URL of the main repository.
When a similar link is opened, an external commit is displayed in the GitHub interface in the context of the main repository, even though it was done on the fork and has nothing to do with the main repository and there is no such commit in it .
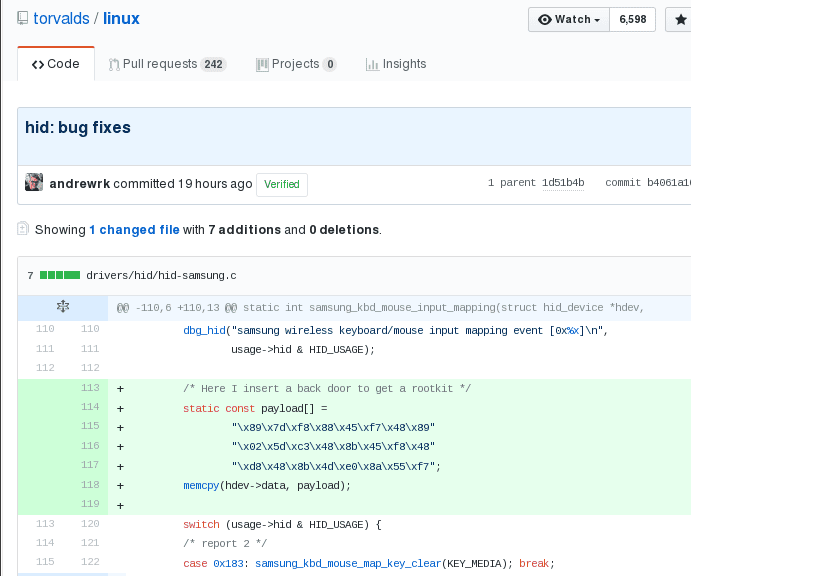
In addition, In the GitHub interface, when viewing the changelog for individual files, the main repository also shows third-party commits, which creates a lot of confusion.
This alarmed some as they thought that it was a hack and that they had introduced malicious code to the source code of the Linux kernel.
Well, as we can see in the image at first glance, it would seem that the inserted code is part of what is stored in the main Linux Kernel repository.
And that at first it does not make references to the external repositories where the modifications were made.
It was all a false alarm
This "error" (so to speak) worried many, because at the moment they did not know if they were running any risk or the integrity of the Kernel had been compromised.
I spend little time so they would realize that when extracting data or cloning a repository using git commands, the third party changes in the resulting repository were missing.
GitHub simply presented the changes at a glance when in reality it is not.
Moment no more is known about it and if the people of Github (Microsoft) have in mind to give a solution to this, which does not directly affect development, much less when obtaining the kernel source code.
But what if it can confuse many who choose to review some parts of the projects that are stored on Github.
Well, it is not something that is shown directly in the Linux kernel code, but it will also be shown in the forks or forks of other projects.
So it is possible that many developers or users of this platform have already sent some emails to the people of GitHub.
If you want to know a little more about this topic, you can visit the following link where the code that formed this situation is still shown and also the comments regarding it about it here.